
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
The familiar scenario plays out countless times each day: you receive a panicked text message. Your bank account has been compromised, or a package awaits but requires a small customs fee. A sense of urgency compels you to click the included link, where the trap lies in wait.
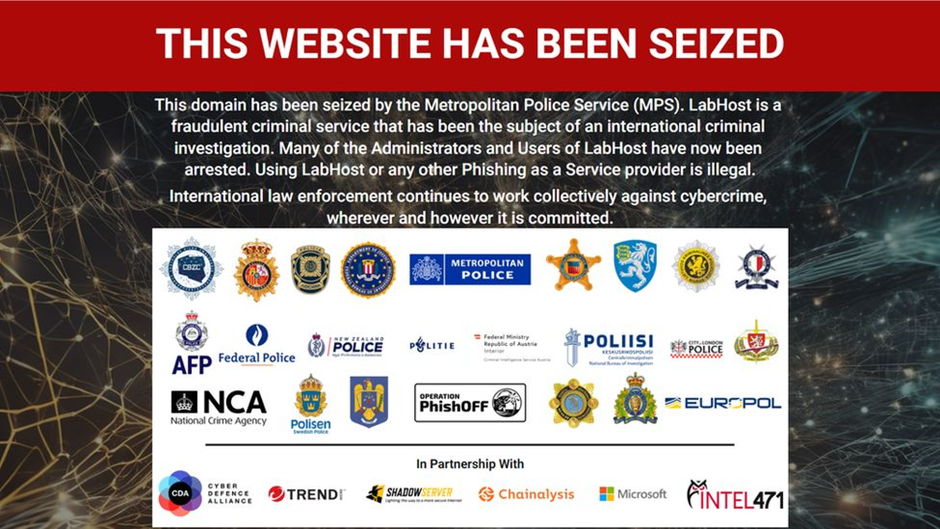
This type of attack wasn’t born of individual hackers but from something far more insidious – LabHost, a criminal marketplace that transformed phishing into a streamlined, industrialised operation. Now, in a major victory for cyber security, LabHost has been shut down after a global law enforcement operation led by the UK’s Metropolitan Police.
LabHost was more than just a website; it was a complete toolkit for fraud. For a monthly fee, it offered:
LabHost’s goal was to make phishing accessible to anyone, regardless of technical skill. It was a recipe for widespread digital theft, with over 40,000 fraudulent websites and hundreds of thousands of victims globally.
A typical LabHost attack exploited familiarity and a sense of urgency:
The LabHost takedown was a testament to international cooperation. Over 19 countries were involved, with arrests made worldwide and the platform’s infrastructure seized. UK authorities played a pivotal role, building the investigation over two years with assistance from Europol, the National Crime Agency, and cyber security experts.
But this is more than just disrupting a single criminal enterprise. Police are actively contacting victims and pursuing leads against hundreds of LabHost users, sending a clear message: the digital underworld is no longer a safe haven.
While the fall of LabHost is a win, vigilance remains crucial. Protect yourself and your business:
The LabHost bust marks a significant step forward, but the war on cybercrime is far from over. Remain informed, stay alert, and remember, the best defence against online scams is a healthy dose of scepticism and a commitment to good security practices.
Further reading on the subject can be found at: