
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
Cyber security experts have recently identified a sophisticated cryptojacking campaign that employs a new type of malware named “GhostEngine.” This malware leverages vulnerable drivers to disable endpoint detection and response (EDR) systems, allowing attackers to remain undetected while they mine cryptocurrency.
GhostEngine is a malware designed to exploit vulnerabilities in legitimate software drivers, a technique known as Bring Your Own Vulnerable Driver (BYOVD). This method allows attackers to disable security measures by loading compromised drivers into the system, which operate with high privileges and can terminate security processes.
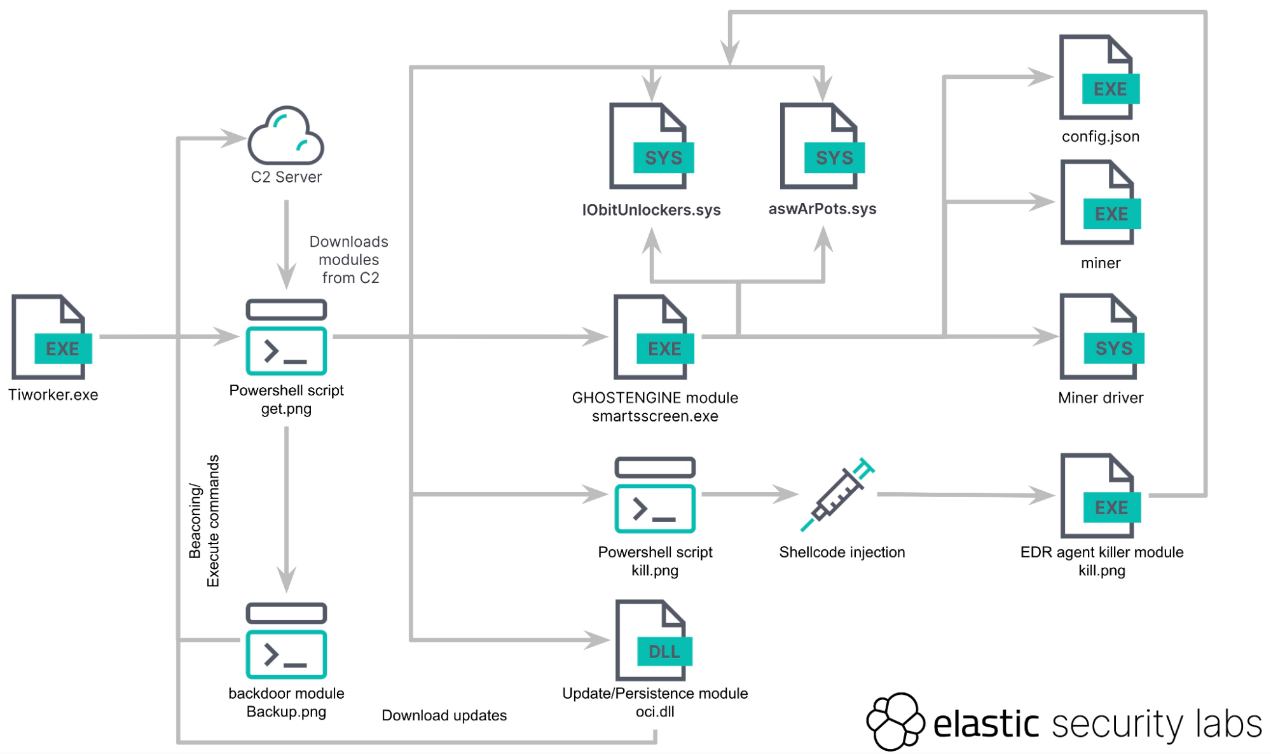
Detecting GhostEngine can be challenging due to its ability to disable logging and security processes. However, certain behaviours and signs can indicate its presence:
The GhostEngine malware represents a significant threat due to its sophisticated techniques and ability to disable advanced security solutions. Organisations must remain vigilant and implement proactive measures, such as updating vulnerable driver blocklists and monitoring for signs of malicious activity. By understanding and anticipating these threats, businesses can better protect their networks and data from such stealthy attacks.
For more in-depth technical details and ongoing updates about GhostEngine, refer to the following sites: