Data Privacy Starts With Cyber Basics
Data Privacy Day is a useful reminder that privacy and cyber security are not separate conversations. You can have the best privacy policy in the…
Phishing attacks are one of the most common methods threat actors use to gain access to your network and devices. If you have an email account or phone number or use any online messaging platform, chances are you have been the recipient of a phishing attack.
Phishing is a type of attack used by hackers that relies on social engineering and deception to get the victim to reveal personal information. This information typically includes login or banking details. Phishing attacks often aim to get malware onto the victim’s device, giving the threat actor behind the attack access to the data on your computer.
Phishing attacks can be sent across almost any online platform that allows messaging. Some of the most common ways a phishing attack can find its way to you include email, text messages and phone calls. However, the rise of social media means that threat actors have started to include popular online platforms in their attacks and have been sending out malicious messages through Facebook, Instagram, Twitter, and LinkedIn, to name a few.
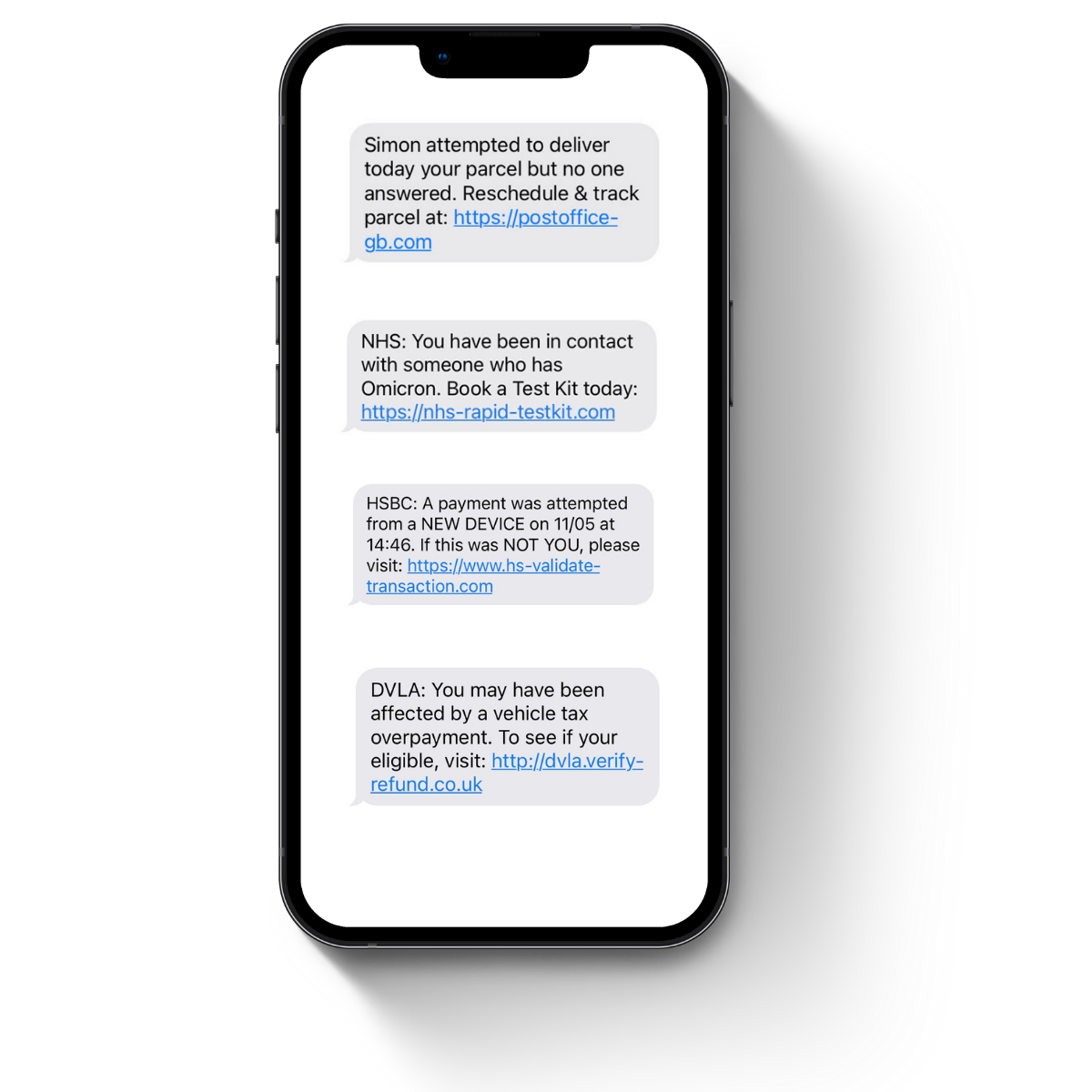
The word ‘phishing’ derives from the idea that the hacker is trying to lure people in with bait – typically structuring their messages around a subject that will grab someone’s attention and make them want to respond quickly. Depending on the platform the attack uses, the bait will come in various forms, but it will all have the same themes that hint that the message is fraudulent. Knowing what to look out for can help prevent you from becoming the next victim of a phishing attack:
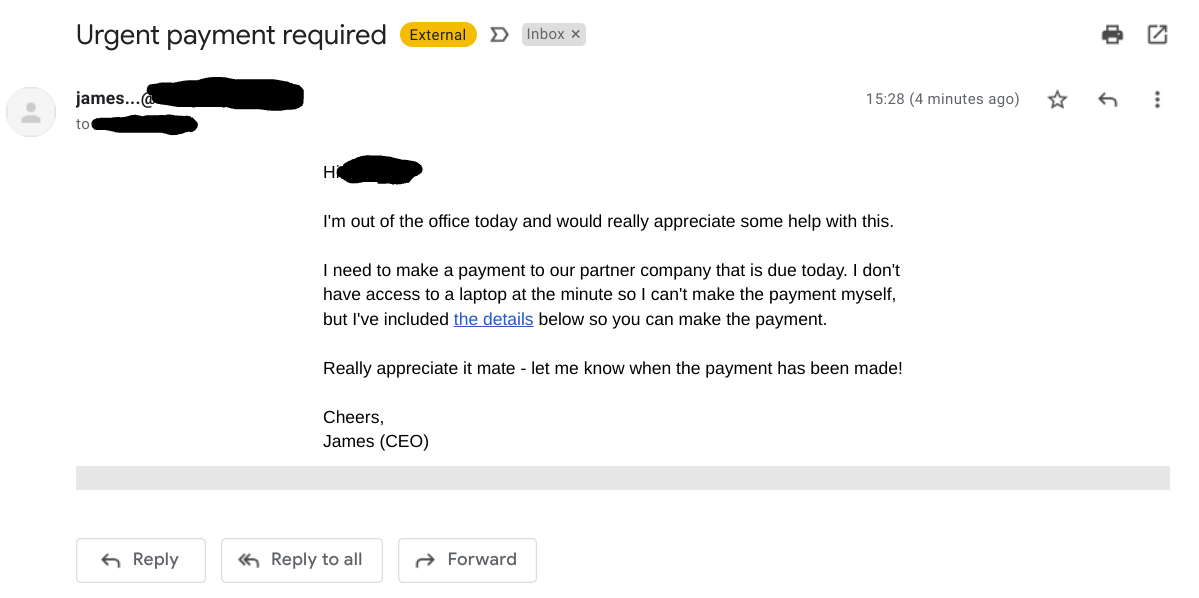
Organisations are often targeted with a more specific phishing attack known as spear phishing. Unlike the generic topics of typical phishing attacks, spear phishing attacks use information gathered by the hacker to make the message more tailored to the target. This may include using your job position and line of work as a subject line or sending out emails that look as though they are from clients or colleagues. If a hacker has access to someone else’s work account, they will send out emails from the compromised login using the victim’s name and position in the company to make the message seem more legitimate.
The content of spear phishing attacks can differ slightly from generic phishing attacks. They don’t always have an urgent tagline or obvious grammatical errors. Instead, they may pretend to be a typical work-related email, such as asking you to complete a financial transaction, sign a document, or watch a training video. If you receive an email that seems suspicious and are unsure of whether to respond to it or not, the best thing to do is to ask the sender in person or over the phone to confirm that the email is legitimate verbally. If that is not possible, ask a colleague or whoever looks after your IT for advice – they may have received similar emails in the past or could spot signs that the email is fraudulent.
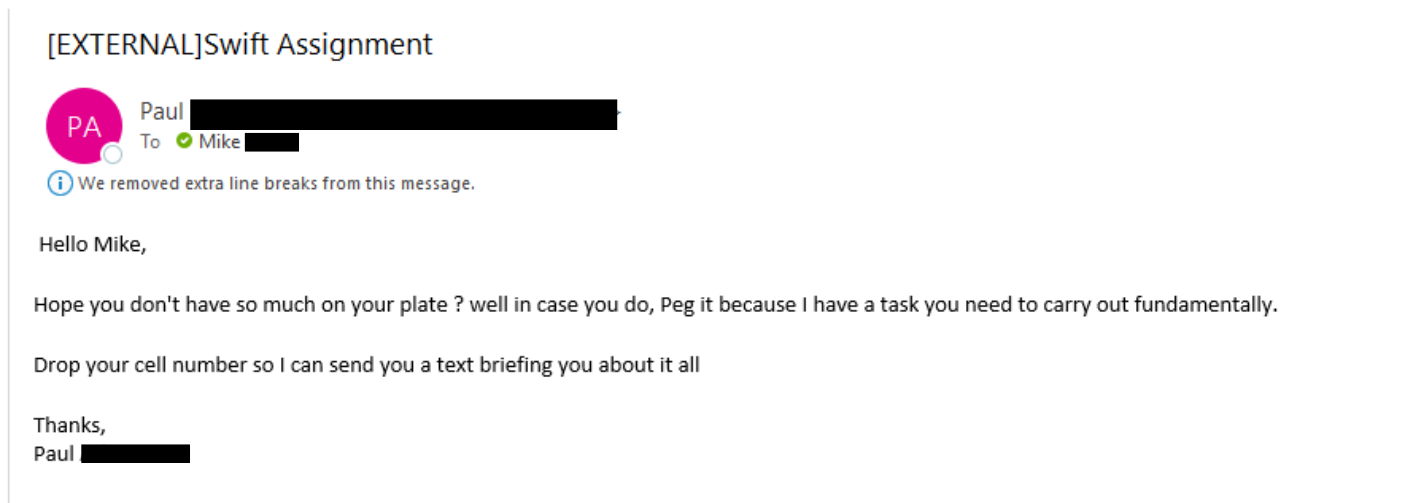
Like spear phishing, whale phishing involves a crafted, specific message. However, whaling attacks are explicitly targeted at senior executives of an organisation, such as chief executives or business owners. As senior leaders are often present on their organisation’s website and social media accounts, hackers can gather a large amount of information about their target’s work and personal life, allowing them to craft a highly tailored message. Because the message is highly targeted, whaling attacks may not only be sent through email but can also be conducted through phone calls and letters – methods of communication not typically seen in standard phishing attacks. A successful whaling attack can have enormous consequences on an organisation, not only in monetary value but also in reputational damage. Senior-level positions often have a large digital reach in an organisation, and a compromised account could give a hacker access to much of a business’s data and systems.