
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
Researchers at Sucuri have published a blog detailing their recent observations of attackers using an outdated and insecure WordPress plugin to create a backdoor into compromised websites. The plugin, EvalPHP, allows for PHP code to be used in WordPress sites, allowing site admins to create code that can run anytime a user opens a web page. EvalPHP has not been updated since 2012 and until recently saw very few (if any) downloads.
However, beginning March 29th, Sucuri researchers noticed that the plugin had seen a resurgence and was seeing downloads spike to over 7,000 a day.
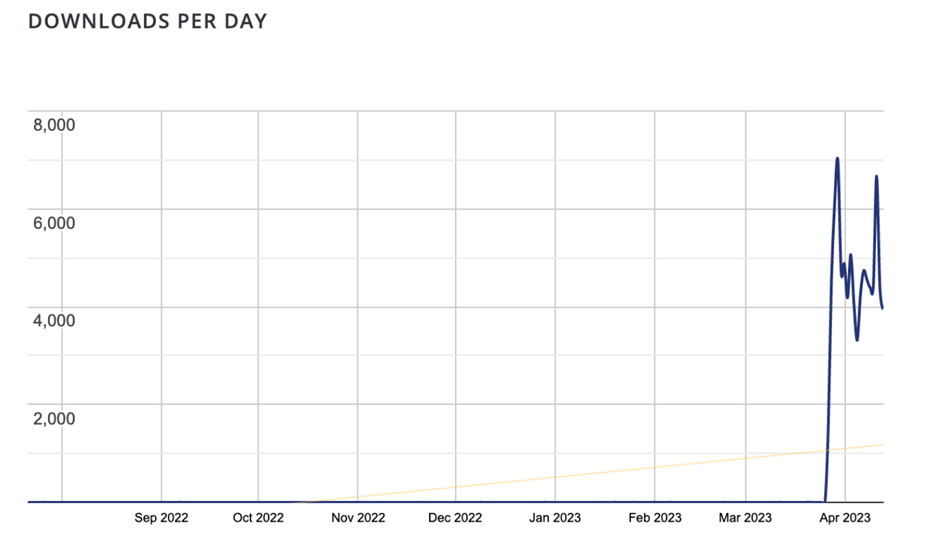
This spike has not been caused by legitimate web developers using an outdated plugin. Instead, hackers are using a vulnerability that allows for the creation of backdoors to an already compromised website.
To carry out this attack, the threat actors need access to the WordPress administrator panel of the website. By default, a website’s WordPress admin login page is publicly available to access, leaving it vulnerable to brute force attacks. Websites that use default, weak, or easily guessable credentials could be compromised without the website owner ever knowing.
With admin access to a site, the attackers can make changes to the website as they please – including downloading plugins. As the Sucuri researchers have seen, attackers have now started using vulnerable plugins to allow for easy, repeated access to the site, even if the administrator credentials are changed, or multi-factor authentication is added to the site.
With EvalPHP, attackers have been seen injecting malicious PHP code into the website’s database and creating a simple test page hidden from the rest of the website. This page will have the malicious EvalPHP code within it, allowing attackers to log in as administrators whenever they visit the site.
With such high-level access to a site, attackers can use it for their own purposes, such as spreading malware, hosting phishing attack landing sites, and bypassing firewalls in other attacks.
To protect your WordPress website from this attack, it is important to first protect your administrator account from becoming compromised. Some of the following steps outline how to do this:
In addition to protecting your administrator panel from becoming compromised, Sucuri researchers recommend the following protections to consider:
https://blog.sucuri.net/2023/04/massive-abuse-of-abandoned-evalphp-wordpress-plugin.html – Published April 19th