
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
The Akira ransomware group, a relatively new player in the cybercriminal landscape, is quickly gaining momentum and expanding its reach. Recent findings suggest that Akira is now targeting Linux systems, shifting from its previous focus on Windows. This move aligns with a growing trend among ransomware actors who recognise the potential for exploiting Linux, which is widely used in enterprise environments, including IoT devices and critical applications.
Previously known for its attacks on Windows systems, the Akira group has evolved tactics and developed a new version of its ransomware specifically designed to exploit open-source Linux operating systems. Cyble Research and Intelligence Labs (CRIL) researchers disclosed this information in a blog post published on June 29.
This strategic shift by Akira demonstrates the increasing vulnerability of Linux systems to cyber threats and ransomware groups’ recognition of the expanding opportunities presented by Linux’s popularity in enterprise environments. Linux has become the preferred choice for running virtual container-based systems, often serving as the backbone for IoT devices and mission-critical applications.
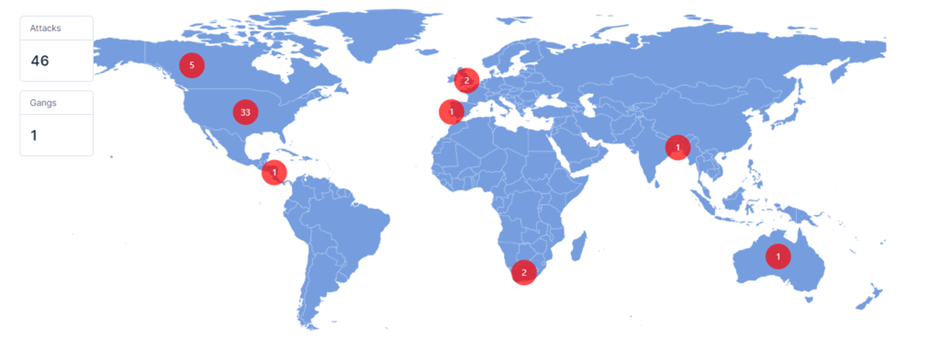
Akira’s expansion into Linux follows a similar trend observed in other well-established ransomware groups such as Cl0p, Royal, and IceFire. The Akira group has already compromised 46 publicly disclosed victims, with the majority in the United States. These victims come from various industries, with education being the most heavily targeted sector, followed closely by manufacturing, professional services, BFSI (banking, financial services, and insurance), and construction. Other victims span a range of sectors, including agriculture, food and beverage, IT and ITES, real estate, consumer goods, automotive, chemical, and more.
Akira’s primary method of operation involves compromising systems and stealing data using double-extortion tactics. They threaten to leak the stolen data on the Dark Web unless the victims pay the ransom demanded.
The new Linux ransomware variant is distributed as a console-based 64-bit executable file written in Microsoft Visual C/C++ compiler. When executed, it retrieves a list of logical drives available on the system using the GetLogicalDriveStrings() API function.
Afterwards, the malware drops a ransom note named “akira_readme.txt” in multiple folders. It proceeds to search for files and directories to encrypt by iterating through them using the FindFirstFileW() and FindNextFileW() API functions.
The ransomware employs the “Microsoft Enhanced RSA and AES Cryptographic Provider” libraries and a hardcoded base64 encoded public key to encrypt the victim’s machine. Encrypted files are then renamed with the “.akira” extension. The encryption process involves utilising various functions from CryptoAPI.
Additionally, Akira ransomware includes a feature that prevents system restoration. It accomplishes this by executing a PowerShell command that initiates a WMI query to delete the shadow copy.
The ransom note dropped by Akira provides instructions for victims to contact the group and negotiate the terms for a ransom payment. To further compel victims to comply, the group displays a list of non-compliant victims and leaks their data on their ransomware site.
Researchers have provided several recommendations to help organisations prevent and mitigate ransomware attacks. These include regularly backing up data and storing backups offline or on a separate network to facilitate system restoration in the event of an attack.
Enabling automatic software updates on computers, as well as other mobile and connected devices, is crucial. Organisations should also employ reliable and trusted antivirus and internet security software across all connected devices.
Furthermore, users should exercise caution when encountering untrusted links and email attachments, verifying their authenticity before opening them, as ransomware is often distributed through phishing attacks.
In the event of a ransomware attack, swift actions can minimise damage to the network. Organisations should immediately disconnect infected devices and any connected external storage devices on the network. Examining system logs for suspicious events is also recommended.
By implementing these preventive measures and following effective response strategies, organisations can strengthen their resilience against ransomware threats.
We have created a Ransomware guide which provides information on the myths around ransomware and how to stay secure.