
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
A new Anatsa mobile malware campaign is targeting UK banking customers and those in Germany, Spain, Netherlands, Slovakia and the Czech Republic. As with most Anatsa campaigns, the malware is distributed through the Google Play Store using “droppers”, seemingly benign applications (apps) that the victim downloads and carries out simple functions. In this campaign the dropper, shown below, is a “phone cleaner” which has over ten thousand downloads, the app has been reported to Google Play and has been removed, but threat actors are known to have multiple dropper apps in the Play Store at any one time.
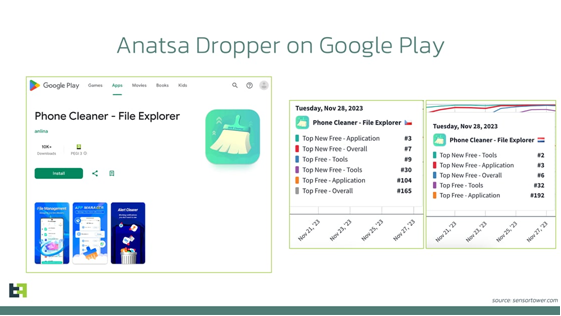
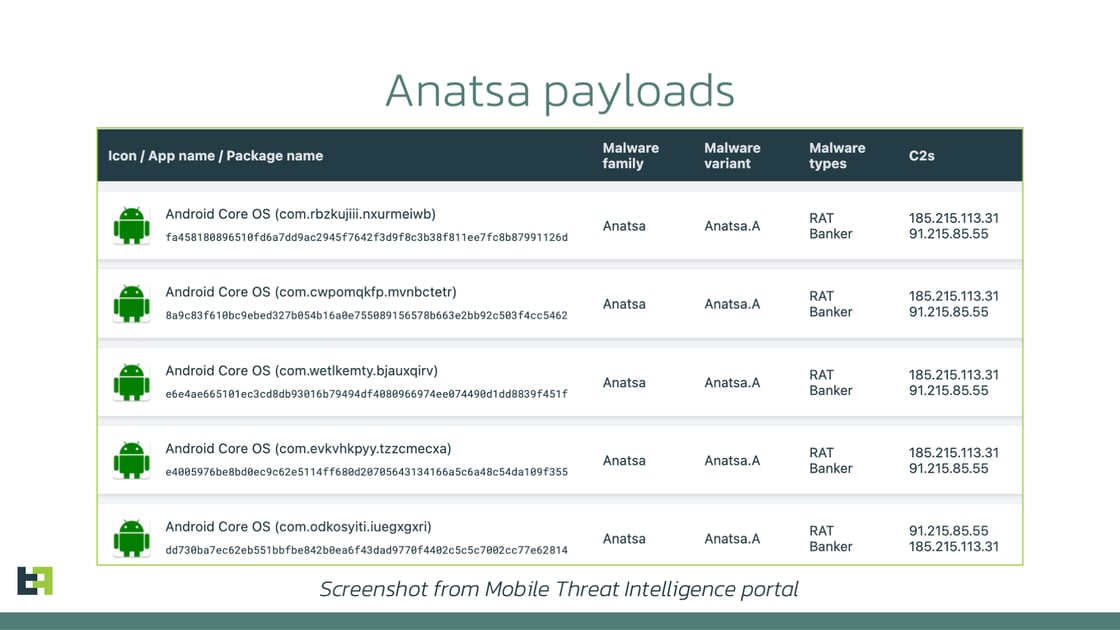
After a period, the app is updated with the malicious component allowing threat actors to capture banking credentials, and credit card information and take remote control of the device. The malicious update in this campaign no longer uses the “PDF AI” icon that has been used by other campaigns in 2023, but instead disguises itself as “Android Core OS”, shown below, possibly in an attempt to draw as little attention as possible.
For further guidance on protecting yourself against mobile malware, view our ‘Mobile Malware’ guide.