
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
A new phishing technique has emerged that cyber criminals are using to steal login credentials from unsuspecting victims. This method involves creating malicious progressive web apps (PWAs) that display fake login forms mimicking well-known brands or services. These PWAs can be installed on a user’s device, making them appear as legitimate applications.
PWAs are web-based applications built using HTML, CSS, and JavaScript. They function like native mobile apps but can be accessed through a web browser and installed on a user’s device. Popular websites like Twitter, Instagram, and Facebook use PWAs to provide a seamless app-like experience to their users.
Cyber criminals are now creating PWAs with convincing corporate login forms to phish for user credentials. These fake PWAs may prompt visitors to “install the app” on their devices. Once installed, the PWA launches and displays a fake login screen, often with a spoofed URL in the address bar to appear more legitimate.
To lure victims into installing the malicious PWA, attackers may:
If a user enters their login credentials into the fake form, the information is sent directly to the attacker.

To avoid falling victim to these attacks, exercise caution when prompted to install any application or PWA, especially from unfamiliar sources.
Here are some tips to stay safe:
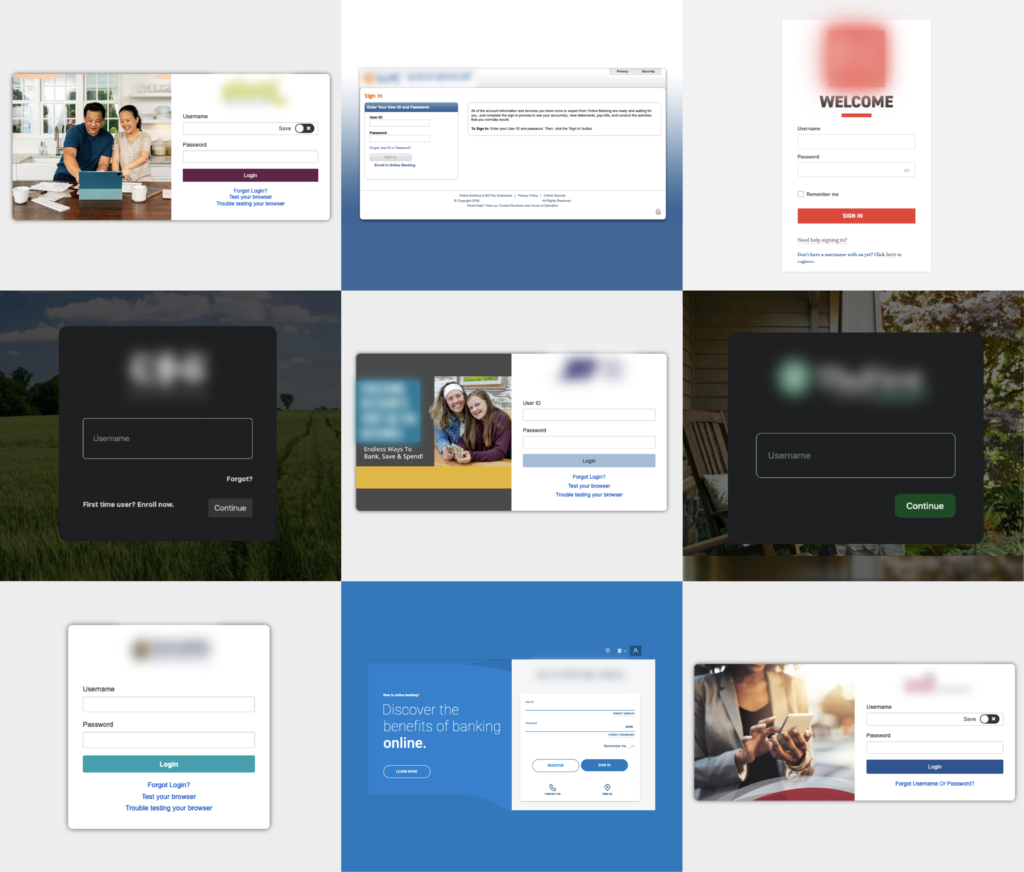
If you suspect you may have fallen victim to a PWA phishing attack, immediately change the passwords for any accounts potentially compromised and enable additional security measures like two-factor authentication. It’s also advisable to monitor your accounts for any suspicious activity and report the incident to the relevant authorities.
While PWA phishing attacks may be more sophisticated, exercising caution and following best practices for online security can help protect you from falling victim to these scams.
Additional information available at: