
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
Card testing attacks, also known as card checking attacks, are a form of fraud where criminals try to determine if stolen credit card information is valid by making small purchases or attempting to authorise a transaction. The preferred method for criminal card testers is using authorisations, which are less likely to be noticed by cardholders. Card testers also use payments but typically choose small transactions to avoid detection. As a result, businesses that facilitate small-value purchases and donation pages are vulnerable targets for card testers.
Between February and August last year, stripe tracked a surge of credit card fraud where threat actors spammed stores and online shopping apps/websites with millions of low/zero-dollar transactions. This allows the threat actors to verify which cards still work; this can cripple both businesses and individuals. During this time period, stripe blocked more than 20 million of these testing attempts per day!
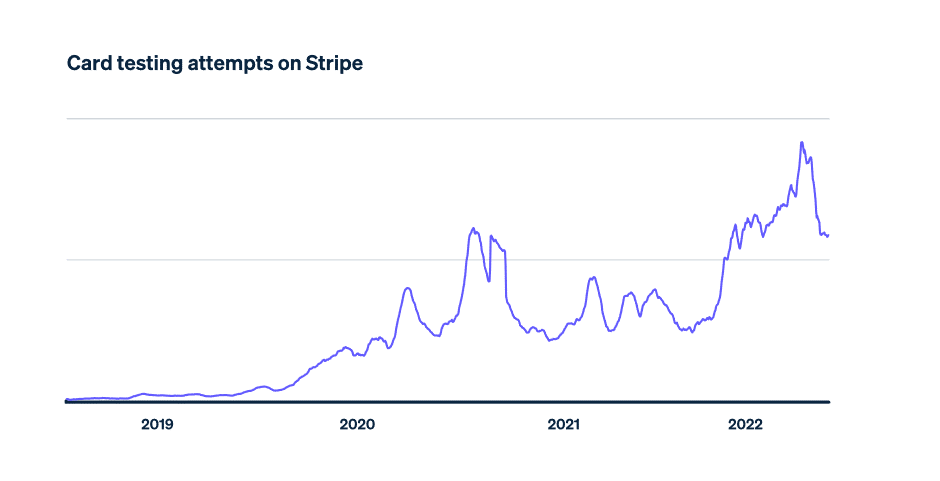
Card testing plays a crucial role in the process threat actors use to extract value from stolen credit card details. When they purchase a list of fraudulently obtained credit card details, they don’t know which cards are still active. Some might have been cancelled and others might have expired. This makes it hard to understand the real value of the list.
This is where card testing comes in. Card testers create programs that automatically attempt to make a small payment with each card in a set or to save it on a site as a validated payment source. Cards that are used or saved successfully can be sold to other criminals who can use them to make larger purchases or manufacture counterfeit cards.
To safeguard your organisation from card testing fraud, it is recommended to implement various protective measures. These include using fraud detection tools, regularly monitoring your account for unusual activities, implementing security measures like web application firewalls (WAF) and utilising a payment gateway to provide a layer of security for your transactions.
An adequate protection solution should provide the following:
Understanding how these crimes are committed, what to look out for, and organisations making minor changes to their payment processes can target an organisation. A WAF and bot management solution can be an effective tool for blocking card testing fraud. They detect and stop suspicious activity before causing harm to merchants, card networks and payment infrastructure.