
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
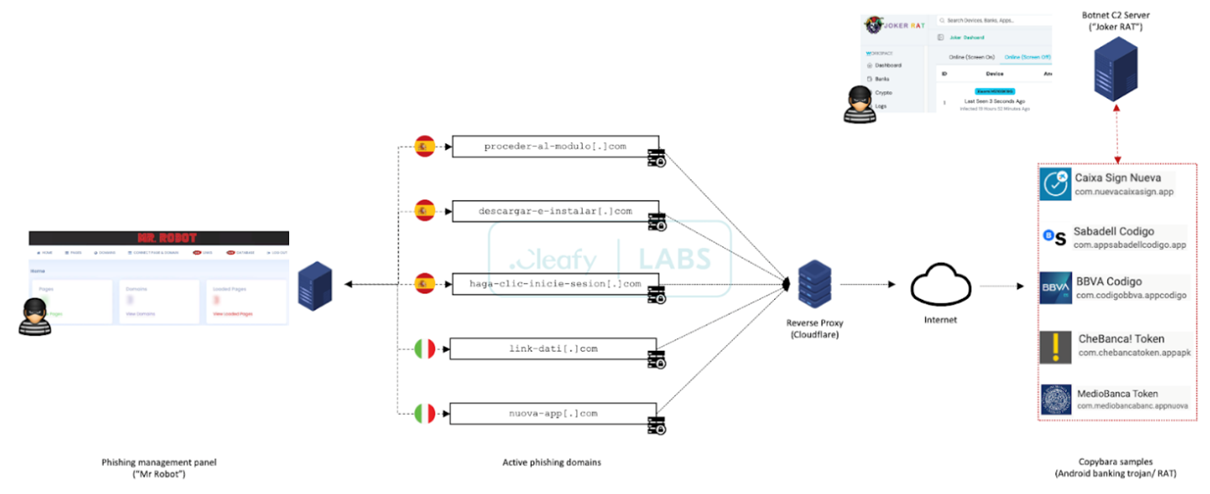
In recent weeks, cyber security researchers have found a concerning Android malware campaign dubbed “Copybara.” This campaign represents an escalating trend in on-device fraud, where malicious software directly compromises victims’ devices to facilitate unauthorised financial transactions.
Copybara is an Android trojan that primarily spreads through malicious applications distributed via third-party app stores. Upon installation, the malware seeks to obtain device administrator privileges, granting it elevated control over the infected device. It then employs overlay attacks, displaying fraudulent login screens or prompts to trick users into divulging sensitive information.
The malware’s primary objective is to hijack legitimate financial applications and initiate unauthorised transactions, enabling cybercriminals to siphon funds directly from victims’ accounts or digital wallets.
Researchers have identified several stages in Copybara’s attack chain:
Copybara’s operators have also been observed leveraging social engineering tactics, such as impersonating legitimate entities or services, to further deceive victims.
To reduce the risk of falling victim to Copybara and similar on-device fraud campaigns, users should:
If a device is suspected of being compromised, users should immediately change their login and security details, notify their banks for advice, and if necessary, seek professional assistance for device remediation. When updating usernames and passwords for bank accounts, do not use the device suspected of being infected, do this on a different phone or laptop for example.
The Copybara campaign underscores the growing sophistication of mobile malware and the need for heightened vigilance and proactive security measures to protect against on-device fraud and other emerging threats.
https://securityonline.info/copybara-fraud-campaign-leverages-on-device-fraud-and-social-engineering-tactics/ https://www.cleafy.com/cleafy-labs/on-device-fraud-on-the-rise-exposing-a-recent-copybara-fraud-campaign?_hsmi=292399610&_hsenc=p2ANqtz-8iMcpUI5-iz6hctNPR69gA3oitZHm54bqtbxXLz3vyR6eaPkHib0tDWUj61c4GPU1c1-kVW1aSywQsC-7-1gwooLcEYyGMDZaLJd0dFbDsChhwkoA