
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
Affected Devices:
Description:
Threat actors have been seen actively exploiting a critical vulnerability within Fortinet’s FortiWeb server, intending to create backdoors to compromised devices for continued access.
The identification of mass exploitation of vulnerable Fortinet devices comes a day after researchers at Horizon3 released proof-of-concept code.
Tracked as CVE-2022-39952, the vulnerability, a remote code execution bug found within FortiWeb servers, was publicly acknowledged in a security advisory by Fortinet on the 16th of February. With a CVSSv3 base score of 9.8, the vulnerability can allow an attacker on the same network as a vulnerable device to access it without any account privileges or user interaction. The Fortinet advisory states that an “unauthenticated, remote attacker to achieve arbitrary code execution via specifically crafted HTTP requests”.
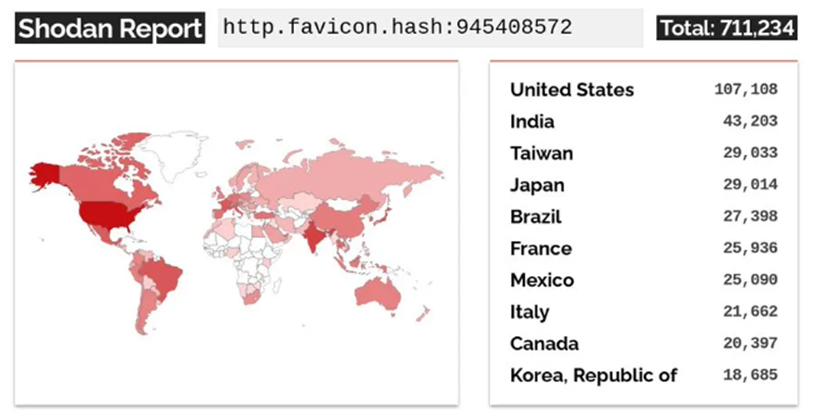
Despite updates being released for the critical vulnerability, researchers at CronUp have detailed in a blog post that they are observing mass exploitation of Fortinet devices. With an estimated 700,000 servers found to be vulnerable, the researchers have warned that a breach of a FortiWeb could allow attackers to gain initial access to the corporate network and may allow for further exploitation and unauthorised access to corporate data. As of the 23rd of February, CronUp reports that they have been seeing attackers using the vulnerability to install a backdoor into compromised devices, allowing attackers to gain access to a device without repeatedly compromising it.
Administrators are strongly recommended to patch this vulnerability as soon as possible, especially if your FortiWeb server is public and internet-facing. Fortinet has released updates for all affected devices; however, there are no known mitigations to prevent this vulnerability at the time of writing.
CronUp’s blog on the vulnerability contains indicators of compromise on this attack, mainly IP addresses that have been seen actively exploiting the bug.
Related Links:
https://www.bleepingcomputer.com/news/security/hackers-now-exploit-critical-fortinet-bug-to-backdoor-servers/ – Published February 22nd
https://www.horizon3.ai/fortinet-fortinac-cve-2022-39952-deep-dive-and-iocs/ – Published February 21st
https://www.cronup.com/explotacion-masiva-de-fortinet-fortinac-cve-2022-39952-rce-no-autenticado-en-progreso/ – Published February 22nd
https://www.fortiguard.com/psirt/FG-IR-21-186 – Published February 16th