
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
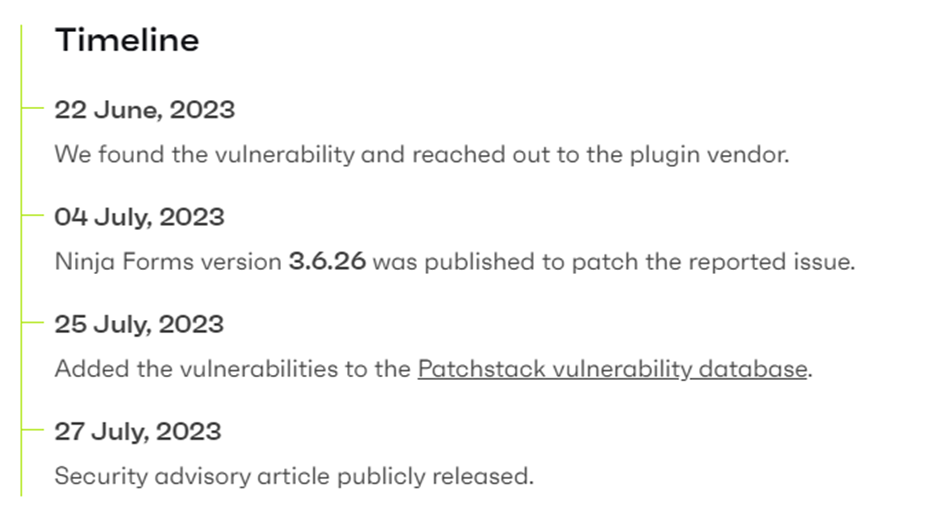
The widely used WordPress form-building plugin, Ninja Forms, has been found to harbour three vulnerabilities. These security flaws could enable attackers to perform privilege escalation and gain unauthorised access to user data, posing a significant risk to the affected websites. Researchers at Patchstack discovered and disclosed the three vulnerabilities to the plugin’s developer, Saturday Drive, on June 22nd, 2023, warning that it affects Ninja Forms versions 3.6.25 and older.
On July 4th, 2023, version 3.6.26 was made available by the developers to address vulnerabilities. Regrettably, despite this update being accessible, statistics from WordPress.org indicate that only around half of the Ninja Forms users have taken the step to download this latest patch. Consequently, approximately 400,000 websites remain susceptible to potential attacks.
Patchstack’s investigation revealed the initial vulnerability, identified as CVE-2023-37979. This flaw involves a reflected XSS (cross-site scripting) vulnerability that operates through POST requests. Exploiting this flaw empowers unauthenticated users to elevate their privileges and pilfer information from privileged users. The attack is executed by deceiving privileged users into accessing a meticulously crafted webpage.
The second and third issues, CVE-2023-38393 and CVE-2023-38386, relate to broken access control problems within the plugin’s form submissions export functionality. These vulnerabilities allow Subscribers and Contributors to bypass proper access restrictions and gain the ability to export all the data submitted by users on the affected WordPress site. As a result, sensitive information becomes accessible to unauthorised individuals, potentially leading to privacy breaches and data misuse.
The identified flaw in the vulnerable Ninja Forms plugin poses a severe risk to any website that supports membership and user registrations. If such sites use an affected plugin version, they become highly vulnerable to potential massive data breaches.
However, the developer addressed these security concerns in version 3.6.26 through several key patches. These patches involve implementing permission checks to rectify the broken access control issues and introducing function access restrictions to prevent the exploitation of the XSS vulnerability. The vendor aims to bolster the plugin’s security and protect websites from potential data breaches and unauthorised access by applying these updates.
Patchstack’s comprehensive coverage provides intricate technical details about the three identified flaws, making it relatively effortless for knowledgeable threat actors to exploit them.
Considering the severity of the vulnerabilities, it is strongly advised that all website administrators utilising the Ninja Forms plugin take immediate action. The recommended course of action is to update to version 3.6.26 or any subsequent releases as soon as possible. If updating immediately is not feasible, administrators should temporarily turn off the plugin on their sites until the patch can be applied. This proactive approach is crucial to prevent security breaches and safeguard user data from unauthorised access or misuse.