
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
Description:
Security researchers at Patchstack have published research detailing multiple vulnerabilities within the popular WordPress plugin LearnPress, a free learning management system plugin for WordPress that allows site owners to develop and host online courses without requiring much programming knowledge. All the vulnerabilities detailed in the article have a critical severity rating and were discovered between 30th November and 2nd December 2022.
CVE-2022-47615 allows an unauthenticated attacker to find local files within the target website and show their output on the screen. This includes files that store sensitive information, such as user data and credentials. Should an attacker access files that store passwords, they may be able to take over the database on the site. This vulnerability has a CVSSv3 score of 9.3 and falls under the sensitive data exposure category, which is third on the OWASP Top 10 list of vulnerabilities. The code for this vulnerability can be found in the file ‘inc/databases/class-lp-db.php’, specifically within the ‘execute’ function.
The second vulnerability disclosed is tracked as CVE-2022-45808 and allows for an unauthenticated user to perform SQL injection. With a CVSSv3 base score of 9.9, this vulnerability allows a user to interact directly with the site’s database, which could allow a malicious user to steal and edit data and create a new administrator account. The vulnerability can also be found within the file ‘inc/databases/class-lp-db.php’, once again in the ‘execute’ function.
The last vulnerability, tracked as CVE-2022-45820, allows for an authenticated attacker to perform SQL injection specifically within two shortcodes of the plugin, ‘learn_press_recent_courses’ and ‘learn_press_recent_courses’. A malicious user would require at least a Contributor role to trigger the vulnerability. Although this vulnerability has a slightly lower CVSSv3 score of 9.1 as it requires authentication to exploit, it should be noted that the previous vulnerability allows an attacker to potentially create an administrator account for their personal use, which makes exploiting this vulnerability relatively easy.
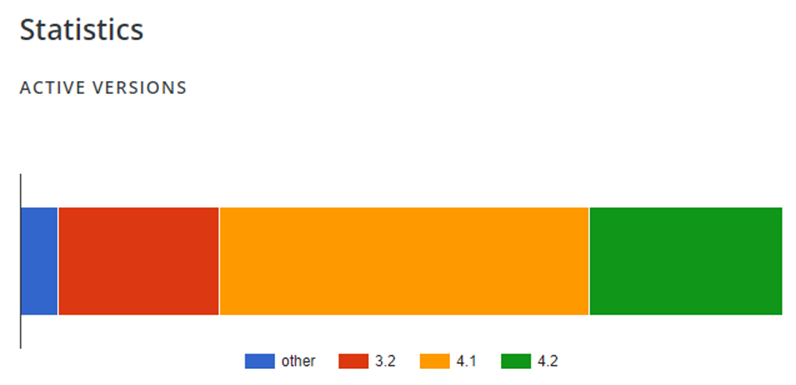
All of the above vulnerabilities are fixed in LearnPress version 4.2, which was released on the 20th December 2022. Despite a patch released over a month ago, only 25% of all sites using the plugin have updated to the latest version, leaving around 75 thousand websites vulnerable to critical file inclusion and SQL injection bugs.
If you use LearnPress on your website, upgrading your site to the latest version is highly recommended to protect against these critical vulnerabilities.
Related Links:
https://patchstack.com/articles/multiple-critical-vulnerabilities-fixed-in-learnpress-plugin-version/ – Published January 24th
https://www.bleepingcomputer.com/news/security/75k-wordpress-sites-impacted-by-critical-online-course-plugin-flaws/ – Published January 24th
https://wordpress.org/plugins/learnpress/advanced/ – LearnPress usage statistics