
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
TBK DVR4104 and TBK DVR4216, and rebrands of these models sold under the Novo, CeNova, QSee, Pulnix, XVR 5 in 1, Securus, Night OWL, DVR Login, HVR Login, and MDVR brands.
Fortinet has released an alert warning of a massive increase in attacks attempting to exploit an authentication bypass vulnerability found in TBK DVR devices.
First discovered in 2018, the critical vulnerability allows an unauthenticated attacker to gain administrator access to the device by simply sending it a HTTP request with a cookie containing the text “uid=admin”, where the device will then respond with its administrator credentials. Only a single command is required to do this, and proof of exploit code has been available for as long as the vulnerability has been publicly known.
Fortinet warns that it has detected over 50,000 attack attempts within a few days, beginning at the end of April.
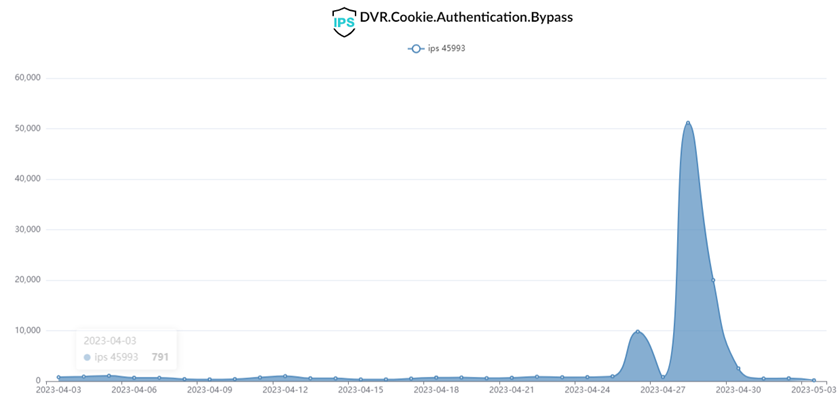
The high number of DVR devices worldwide causes significant concern, especially as these devices are used for security monitoring of businesses. According to Shodan, over 11,000 potentially vulnerable devices are internet-facing.
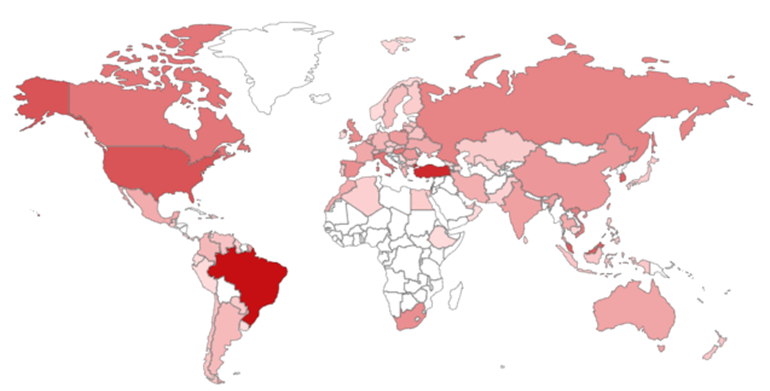
As no security update is available for these patches, there are concerns that many devices will quickly become compromised without their owners ever realising. Because of this, it is suggested that businesses using DVR devices, or the other systems known to be rebranded models of DVR cameras, should replace these vulnerable systems with new models or isolate them from the internet to prevent unauthorised access.