
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
The Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) have released an advisory detailing the actions of a newly detected ransomware dubbed ‘Zeppelin’.
The malware, which was recently first detected by the FBI in June 2022, has been seen encrypting files on victim devices multiple times, therefore requiring multiple decryption keys to regain access to the data. Additionally, the FBI warns that threat actors deploying Zeppelin ransomware will download data before encrypting it, going on to sell the data online or threaten to release it in the event a victim refuses to pay the ransom, as can be seen in their ransom note.
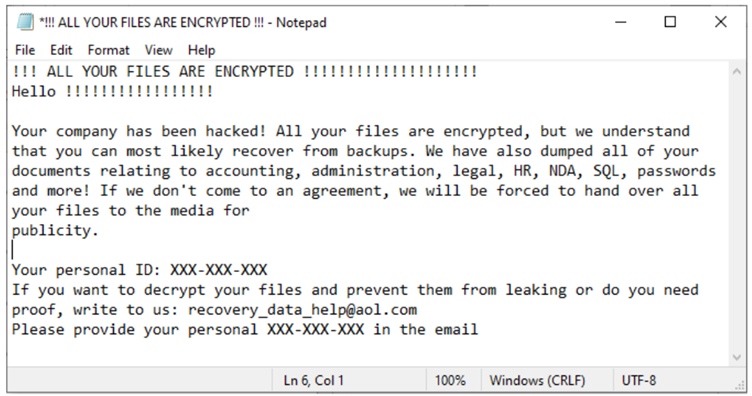
Some of the notable ways threat actors deploying Zeppelin gained access to victim’s network was through phishing campaigns, exploiting vulnerabilities in public-facing systems (notably SonicWall firewall), and RDP exploitation. The FBI adds that threat actors will typically spend a few weeks mapping the victim network, specifically looking for cloud storage and backup systems
A full technical description, as well as indicators of compromise for this malware, can be found here.
Some of the best steps to take to stay protected against any ransomware include:
The FBI has also released the indicators of compromise and attack techniques for this malware. If possible, consider setting up systems that can detect hashes and activity related to this attack.
As threat actors deploying this attack have been seen spending time looking around victim networks prior to deploying the ransomware, keep on the lookout for suspicious and unusual activity within your network. This may include connections from unusual IP addresses, multiple login attempts, and unusual changes to user accounts and system settings.
The FBI also specified that threat actors were specifically targeting SonicWall vulnerabilities. Should you use SonicWall firewall, check that your SonicWall systems are on the latest versions, and update as soon as possible if not.
https://www.cisa.gov/uscert/ncas/alerts/aa22-223a – Published August 11th