
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
Researchers at Accenture’s Cyber Threat Intelligence team have written a report documenting a surge in the popularity of information stealing (infostealer) malware on the dark web.
The spike in infostealer’s popularity is not only down to the ability to harvest usernames and passwords from infected devices but is also because of the malware’s ability to harvest cookie data, which can allow threat actors to bypass multi-factor authentication (MFA). The rise is also due to the popularity of compromised credential marketplaces, where threat actors can buy and sell stolen credentials. The researchers noted that there had been an increase in the number of credentials for sale between July and October 2022, with one of the most popular sites seeing a 40% increase in sales in that time – jumping from 3.3 million to 4.5 million logs available for sale.
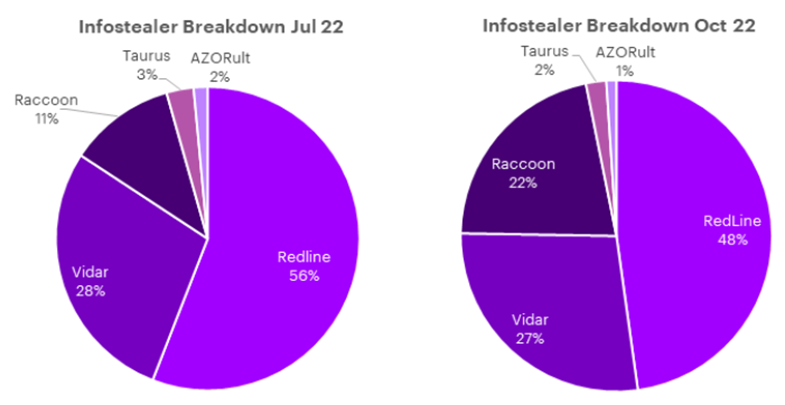
The researchers were also able to document the infostealing malware most seen in attacks between July and October 2022, with the malware variant RedLine being used the most by threat actors.
Preventions:
Malware can pose a significant risk to individual devices, organisations, networks, and services. Some types of malware are designed to look for other devices connected to the network of the host device to infect. This may be not only laptops and PCs but also servers and internet-of-things devices. An infected device brought into a work environment can pose a significant security risk and could allow malicious users into your network.
To protect your organisation against malware:
Related Links:
https://www.accenture.com/us-en/blogs/security/information-stealer-malware-on-dark-web – Published 5th of December
https://www.cybersecuritydive.com/news/infostealer-malware-surge-dark-web-mfa-fatigue-attacks/637977/ – Published 5th of December