
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
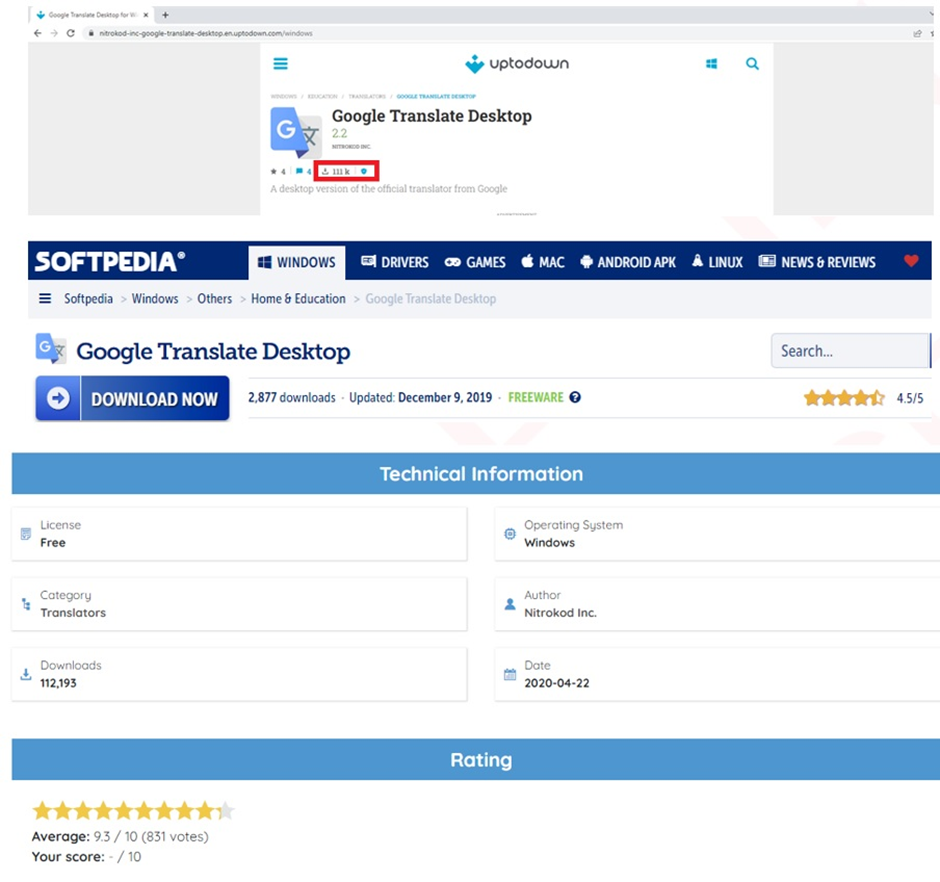
Researchers at Check Point Research have uncovered malware disguised as multiple legitimate apps, including Google Translate and YouTube Music for Desktop. If downloaded, the malware waits for a month to deploy its malicious crypto mining software. The applications are a replica of the legitimate apps and deliver the same service; users downloading the fake apps are unaware of the malicious code running in the background.
Created by a Turkish software company called Nitrokod, the apps have not only been made available on the original creator’s sites but have also been posted on other popular software sites where they claim to have over one hundred thousand downloads.

The malware also has multiple other ways of avoiding detection. Researchers reported that there are six stages the program goes through before finally downloading the crypto mining part of the software. Additionally, the code has multiple delayed scheduled tasks that give the malware’s threat actors time to clear evidence.
To maintain persistence, the program runs scheduled tasks every time the host device is started up, allowing it to run the crypto mining software and consistently check that the malicious side of the program still exists, re-downloading it if not. Notably, the malware can avoid detection by waiting for four different system start-ups on four different days, meaning it could take weeks for the malicious code to deploy.
The full technical report on this malware can be found here.
Preventions:
The following steps can help you remove this malware:
Malware can pose a significant risk to individual devices, business networks, and services. Some types of malware are designed to look for other devices connected to the network of the host device to infect. This may not only be laptops and PCs but also servers and internet-of-things devices. An infected device brought into a work environment can pose a significant security risk and could allow malicious users into your network.
To protect your organisation against malware:
Related Links: