
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
Description:
Scans conducted by researchers at internet security company Shadowserver have shown that over 60,000 Microsoft Exchange servers are still vulnerable to two vulnerabilities, CVE-2022-41082 and CVE-2022-41040, collectively dubbed as ProxyNotShell. Microsoft first addressed the vulnerabilities in September 2022 and released a security update for them in November 2022.
However, the full internet scans conducted by Shadowserver have shown that many servers have not yet been updated to patch the issue.
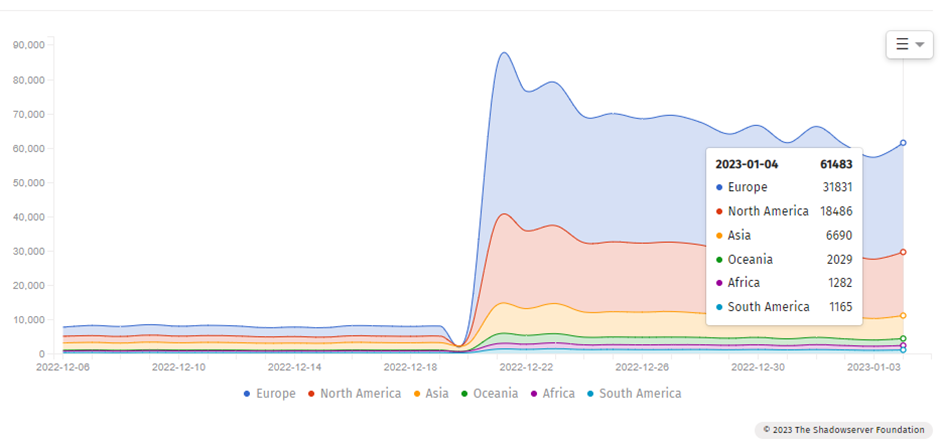
The scans show that over half of all vulnerable servers are within Europe at the time of writing. With a mapped version of the data, it can be seen that around 4,000 of these servers are within the UK.
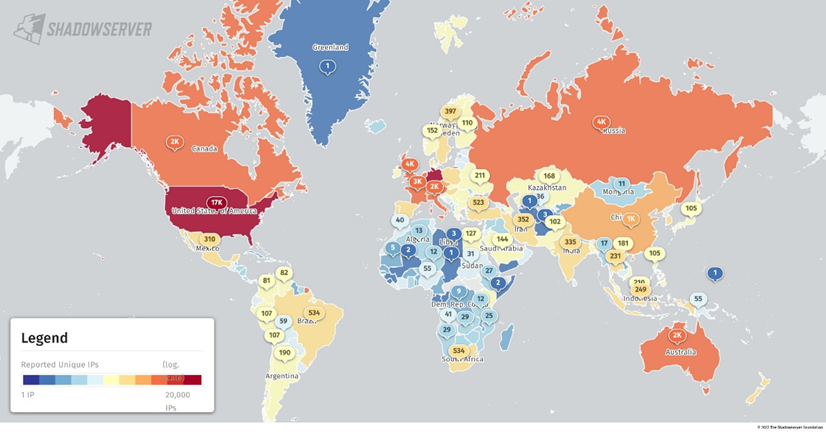
The data used for the above graphs were collected through scans of the IPv4 internet addresses, and the assessment of vulnerable servers was made based on the returned x_owa_version HTTP header. More about the variables used to discover the servers can be found here.
A potential reason for the high number of vulnerable servers may be that Microsoft initially recommended mitigations for customers who could not update their servers at the time. However, the organisation has since updated the guidance article for the vulnerabilities stating that “The options described in the Mitigations section are no longer recommended.”
As discovered by the cybersecurity organisation Crowdstrike, the original mitigation advice from Microsoft to add a custom URL rewrite rule to block known attack patterns can be bypassed. Crowdstrike said that the new method to exploit the ProxyNotShell vulnerabilities was discovered in investigations into several ransomware attacks. The common entry vector used by the threat actor was confirmed to be Microsoft Exchange.
Successful exploitation of the ProxyNotShell vulnerabilities can lead to attackers escalating privileges and gaining the ability to execute code remotely. However, threat actors require authenticated access to the server to exploit the vulnerabilities successfully.
Preventions:
The ProxyNotShell vulnerabilities only affect customers using on-premise Microsoft Exchange Servers. If you are using Microsoft Exchange Online, you do not need to take any action.
The best way to protect your Exchange server from being exploited is to install the security update released in November 2022. You can find links on how to get and install the update here.
If you are unable to apply patches for this vulnerability, Crowdstrike recommends disabling remote PowerShell for non-administrative users where possible, as well as using web application firewalls to block and monitor any incoming malicious traffic.
Please note that the previously recommended mitigation to ProxyNotShell attacks, which was to add a blocking rule in “IIS Manager -> Default Web Site -> URL Rewrite -> Actions” to block known attack patterns, is no longer recommended by Microsoft and can be bypassed.
Related Links:
https://www.bleepingcomputer.com/news/security/over-60-000-exchange-servers-vulnerable-to-proxynotshell-attacks/ – Posted January 3rd
https://twitter.com/Shadowserver/status/1607439237615419400 – Posted December 26th
https://www.shadowserver.org/what-we-do/network-reporting/vulnerable-exchange-server-report/ – Posted December 23rd
https://dashboard.shadowserver.org/statistics/combined/time-series/?date_range=30&source=scan%2Bscan6&tag=exchange&style=stacked – Dashboard for vulnerable servers