
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
Affected Systems:
Microsoft Exchange Server 2013, Exchange Server 2016, and Exchange Server 2019
Description:
Researchers at cybersecurity firm GTSC have discovered two new zero-day vulnerabilities affecting Microsoft Exchange Server 2013, 2016, and 2019. The first vulnerability, tracked as CVE-2022-41040, can allow an authenticated attacker to run PowerShell within the context of the system, while the second, CVE-2022-41082, allows for an attacker to execute code remotely. Notably, CVE-2022-41040 must be successfully exploited to trigger CVE-2022-41082; however, the exploit only needs the credentials of a standard user to be successful. Threat actors can often obtain credentials using several attacks, including phishing or data breaches, meaning that this vulnerability may catch the eye of cybercriminal’s already in possession of Microsoft users’ login details.
Microsoft has confirmed that Exchange Server is vulnerable to both of these zero-day exploits and has since released mitigation and detection information for both exploits. However, at time of writing, there is no security update to patch the vulnerabilities. Microsoft has stressed that they are “working on an accelerated timeline to release a fix” in an article outlining mitigations against the vulnerabilities.
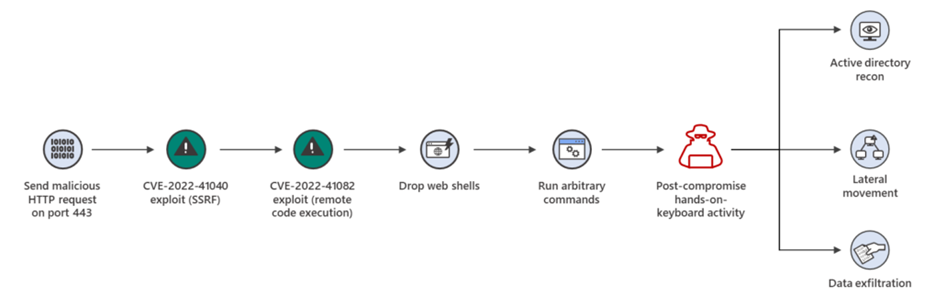
GTSC researchers first detected the vulnerability at the start of August 2022, and Microsoft has shared that they have observed attacks on fewer than ten organisations globally; however, attacks may start to increase as the zero-day have been announced publicly.
The attack detected by GTSC involved a malicious HTTP request sent to port 443:
autodiscover/[email protected]/<Exchange-backend-endpoint>&Email=autodiscover/autodiscover.json%[email protected]
The malicious HTTP request was written in the same format as a ProxyShell exploit; however, it was sent and successfully exploited on an Exchange server on the latest update. The attack was suspected to be from a threat actor based in China.
Post-exploit actions from the threat actor included creating backdoors on the victim’s system, collecting information about the victim’s network, and downloading malicious code onto the victim’s compromised Exchange Server.
Preventions:
Microsoft has stressed that Microsoft Exchange Online customers do not need to take any action, only those running an Exchange server on-premise.
Microsoft has released a script to apply mitigations against the first vulnerability, CVE-2022-41040, which can be found at https://microsoft.github.io/CSS-Exchange/Security/EOMTv2/
Additionally, Microsoft has released some mitigations for customers using Microsoft 365 Defender:
Indication of compromise and detection methods can be found in GTSC’s article on the vulnerabilities here.
Related Links:
https://www.microsoft.com/security/blog/2022/09/30/analyzing-attacks-using-the-exchange-vulnerabilities-cve-2022-41040-and-cve-2022-41082/ – Published 30th September