
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
In targeted phishing attacks that bypass email security gateways, attackers employ encrypted RPMSG attachments sent through compromised Microsoft 365 accounts to steal Microsoft credentials.
RPMSG files are encrypted email message attachments generated using Microsoft’s Rights Management Services (RMS), which provide an additional safeguard for sensitive information by limiting access solely to authorised recipients.
To access these encrypted RPMSG attachments, recipients must authenticate using their Microsoft account credentials or acquire a one-time passcode to decrypt the contents.
The RPMSG are now being used through the authentication requirements to trick users into handing over their Microsoft 365 credentials using illegitimate login forms.
The malicious emails from the threat actors prompt the targets to click on a “Read the message” button to decrypt and access the protected message. This action redirects them to an Office 365 webpage where they are prompted to sign in to their Microsoft account.
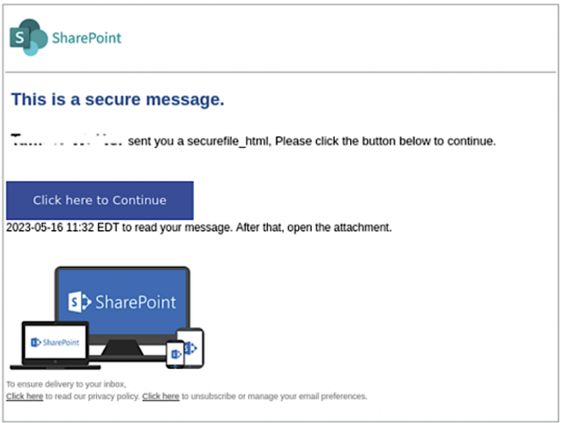
Once the recipients authenticate themselves through this genuine Microsoft service, they can view the phishing email from the attackers. Upon clicking a “Click here to Continue” button, they are directed to a counterfeit SharePoint document hosted on Adobe’s InDesign service.
After clicking “Click Here to View Document,” users are directed to a final destination where they are presented with an empty page and a deceiving “Loading…Wait” message in the title bar. This distracts while a malicious script secretly gathers various system information.
The harvested data includes the visitor ID, connect token and hash, video card renderer details, system language, device memory, hardware concurrency, installed browser plugins, browser window specifics, and operating system architecture.
Once the script completes the data collection process, a replicated Microsoft 365 login form appears on the page. Any usernames and passwords entered into this form are transmitted to servers controlled by the attackers.