
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
Researchers at Proofpoint have discovered various ways cybercriminals can use Microsoft Teams to trick people or infect their computers with harmful software. They found that hackers can use certain features in Teams to deceive users without them realising it. One method involves using tabs in the Teams interface, where hackers can potentially activate a harmful programme or lead users to dangerous websites without leaving noticeable evidence.
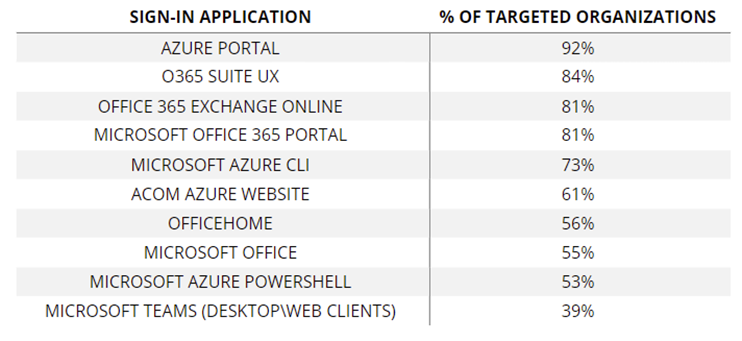
Microsoft Teams is one of the most targeted sign-in applications, with almost 40% of targeted organisations having at least one unauthorised login attempt trying to gain access.
Abusing the default tabs mechanism
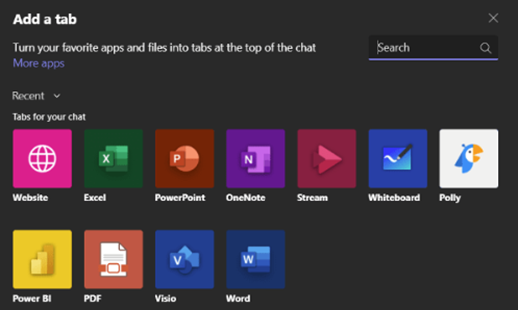
The Microsoft Teams platform allows users to send personal and group messages using Teams channels or chats. Within these channels or chats, different applications can create additional tabs. For example, a default ” Files ” tab is associated with SharePoint and OneDrive. By manipulating these tabs, it can be part of a powerful and primarily automated attack method, especially after an account has been compromised.
Typically, users have the ability to rename tabs as they wish, as long as the new name doesn’t conflict with an existing tab’s name (e.g., “Files”). Additionally, users are supposed to be restricted from reordering tabs in a way that places them before default tabs (e.g., “Files”).
However, by using undocumented Teams API calls, attackers can change the order and name of tabs, allowing them to replace the original tab with a new custom tab. One way that this feature can be leveraged by attackers is by using a native app, “Website”, which allows users to pin a chosen website as a tab at the top of a Teams channel or chat. After pinning a “Website” instance as a tab, an attacker can manipulate the tab’s name, changing it to an existing tab’s name and then repositioning it. This effectively allows the attackers to push the native tab out of view, increasing the chances of using the fraudulent tab.
It’s important to understand that the method mentioned above can only be carried out if the hacker already has access to a compromised user account or Teams token. However, alarming statistics show that around 60% of Microsoft 365 users experienced at least one successful incident of their accounts being taken over in 2022. As a result, if these methods become more widespread, it would give hackers an effective way to move within a compromised system after gaining initial access.
The analysis of previous attacks and current trends in the ever-evolving cloud threat landscape indicates that attackers increasingly use more advanced attack methods. They are adopting new techniques and tools that expose organisations to a range of critical risks when combined with existing security vulnerabilities, including risky functionalities in first-party apps.
Here are some ways to protect your organisation from phishing and malware risks associated with Microsoft Teams:
It’s important to remember that threat actors always seek new ways to steal user credentials and gain unauthorised access. Microsoft Teams, a legitimate and popular cloud application, can be targeted as a platform for various cloud attacks. Stay vigilant and take precautions to protect your organisation’s data and users.