
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
Description:
Researchers at ESET have documented in a report a new form of malware with a wide range of spying capabilities that can act as a backdoor to systems it infects.
Named Dolphin, the malware is maintained and used by a North Korean threat group known as ScarCruft (also tracked as APT37 and Reaper), whose targets include governmental organisations and companies in industries linked to the interests of North Korea.
The researchers reported that the malware uses an exploit in Internet Explorer to get into devices and then proceeds to download a backdoor (known as BLUELIGHT and seen in previous attacks by this threat actor) which is used to install the Dolphin malware, which is a Windows executable written in C++.
Once installed, Dolphin collects information about the host device and its capabilities. The data collected includes the username and computer name, the local and external IP address, a list of installed security products, the operating system version, and if any cybersecurity inspection tools are installed, such as Wireshark. Dolphin uses Google Drive to communicate with the threat actor and upload its findings.
Once initial information about the device is found, the malware searches further for data and devices connected to the device. It exfiltrates data from fixed and non-fixed drives (such as USBs), specifically looking for documents, emails, and other media. The malware also searches for portable devices connected to the victim’s device, such as smartphones. If any devices are found, the malware can exfiltrate files from them.
Additionally, Dolphin can log keystrokes specifically for chrome and internet explorer and take screenshots at regular intervals – the researchers noted that the default is once every 30 seconds. Dolphin’s interactions with browsers also extend to retrieving saved passwords and cookies. If a Google account is found to be logged in, the malware can modify the settings and change the account’s security configurations. Doing so allows the threat actors to access the victim’s emails.
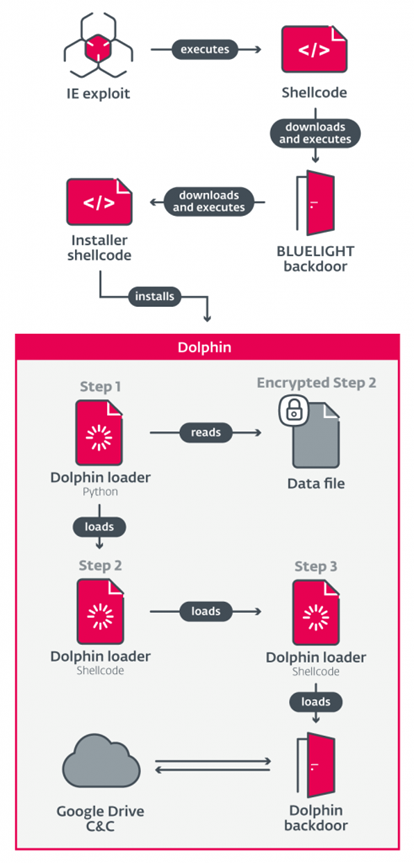
Notably, the main functionality of Dophin is to act as a backdoor, allowing threat actors continued access to the compromised device. All of the above functionality can be extended with commands from the threat actor, which are also sent through Google Drive.
Dolphin’s persistence capabilities include periodically checking that the malware’s loader runs every time the device is started.
Preventions:
The current version of the Dolphin malware targets vulnerabilities found within Internet Explorer. If you still use internet explorer, consider updating to Microsoft Edge (the replacement for Internet Explorer).
The researchers at ESET have provided a list of indicators of compromise for this malware, which can be found here.
Malware can pose a significant risk to individual devices, business networks, and services. An infected device brought into a work environment can pose a considerable security risk and could allow malicious users into your network.
To protect your organisation against malware:
Related Links:
https://www.welivesecurity.com/2022/11/30/whos-swimming-south-korean-waters-meet-scarcrufts-dolphin/ – Published 30th November