
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
Researchers at a cyber security firm Resecurity have released a report outlining a new Phishing-as-a-service (PhaaS) platform advertised on the dark web. Named EvilProxy, the service allows threat actors to easily conduct phishing attacks which bypass multi-factor authentication (MFA) without the skill or technical knowledge typically required to create these attacks.
A video released by the threat actors operating EvilProxy shows how easily the service can be used. Threat actors only have to pay a minimum of $400 (£350) to create phishing attacks with the ability to mimic login pages for several tech organisations, including Microsoft, Google, Facebook, Twitter, GitHub, and Apple, amongst others.
Notably, EvilProxy can allow for a single phishing campaign to use multiple spoofed login sites, as well as allowing up to 10,000 phishing campaigns to run at once from a single profile.
Researchers pointed out that the inclusion of GitHub attacks to the service may allow threat actors to conduct targeted supply chain attacks which aim to compromise repositories belonging to software developers and engineers, which use their legitimacy to gain access to end users’ devices and spread malware.
To conduct attacks that can bypass MFA, EvilProxy operates using what is known as the ‘Reverse Proxy’ concept. A significant flaw in the MFA process, the concept involves leading victims to a phishing page where they are prompted to sign in. Should MFA be enabled on their account, the service fetches the legitimate MFA page from the organisation it mimics and displays to the user. Once MFA is completed by the user, the service detects the cookies used to authenticate the login session and harvests them for the threat actors to use later, giving them the ability to bypass MFA.
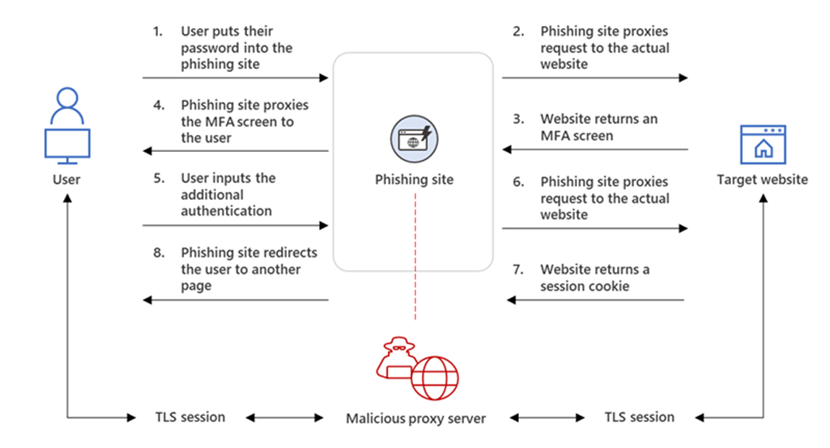
As EvilProxy is so easy to use, instances of reverse proxy phishing attacks may increase dramatically as low-skilled hackers take advantage of the platform, including easy-to-follow instructions on how to set up and manage a phishing campaign.
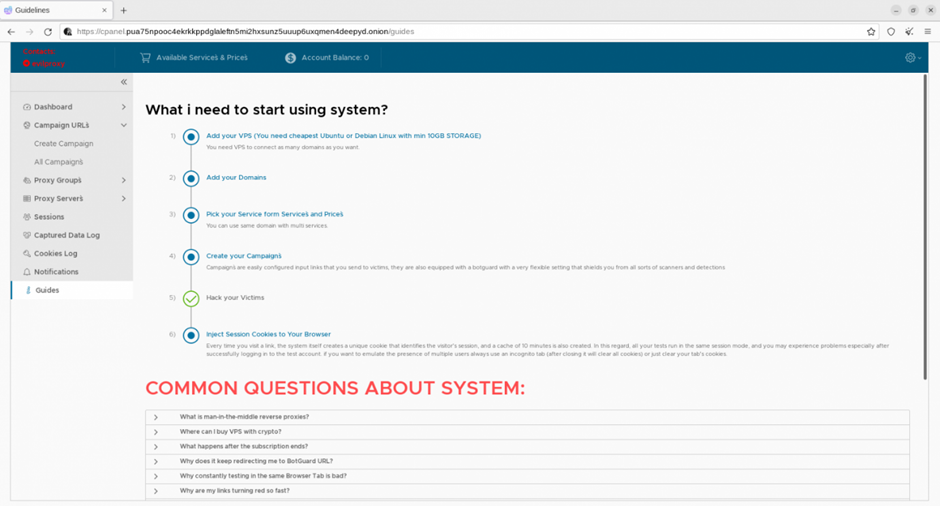
The full Resecurity report on EvilProxy can be found here.
Preventions:
Phishing attacks are one of the most used methods by hackers to gain access to a system. To reduce the chances of a phishing attack from becoming successful, follow these steps:
Resecurity has released some domains and IP addresses associated with EvilProxy from their detection systems. Blocking these domains and addresses can help protect your network from being attacked. However, it should be noted that threat actors dynamically change the IP addresses and domains used in their campaigns to avoid detection, so this list is not definitive.
Related Links:
https://resecurity.com/blog/article/evilproxy-phishing-as-a-service-with-mfa-bypass-emerged-in-dark-web – Published September 5th