
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
Description:
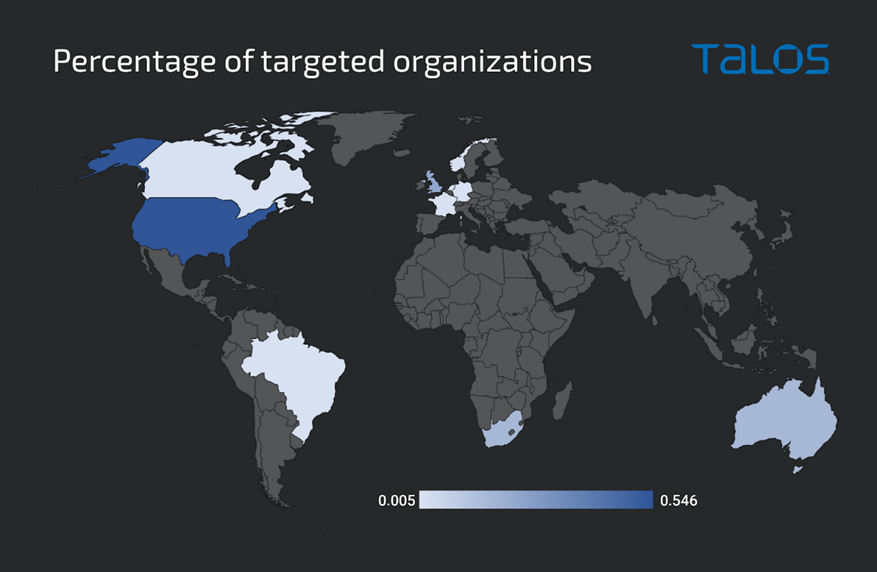
A new phishing-as-a-service (PaaS) tool named “Greatness” is exclusively targeting companies in the UK, US, Canada, Australia, and South Africa, with Microsoft 365 phishing pages that can bypass multi-factor authentication. In a new report published by Cisco Talos, researchers have detailed that they have been tracking several phishing campaigns since mid-2022 using the tool. They have found that this new tool is used almost exclusively for targeting businesses using Microsoft 365.
Most of the campaigns observed began with victims receiving a malicious email containing a HTML file as an attachment, which would supposedly be a shared business document. Once opened, the file would load a Microsoft 356 login page pre-filled with the victim’s email address.
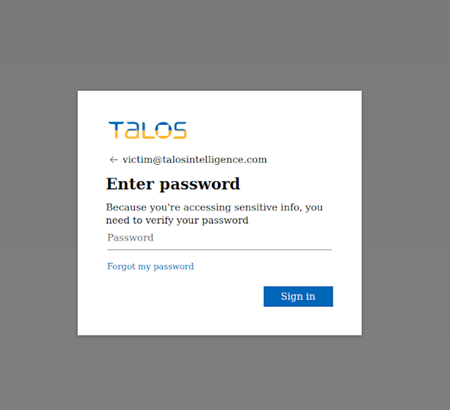
Once the victim had entered a password, the phishing tool would check if they were using multi-factor authentication (MFA) and pull up a fake MFA page if they were. Once an MFA code had been entered, the tool would automatically use it to legitimately log in to the victim’s account, stealing the authentication session cookies. This method allows them to bypass the MFA barrier that is typically difficult for attackers to get past, all while leading the victim into further thinking that their account is safe. Notably, the tool uses the messaging app Telegram to deliver the stolen credentials and cookies to the attackers.
By gaining access to a user account on a corporate network, attackers can deploy more dangerous attacks, such as ransomware or infostealers.
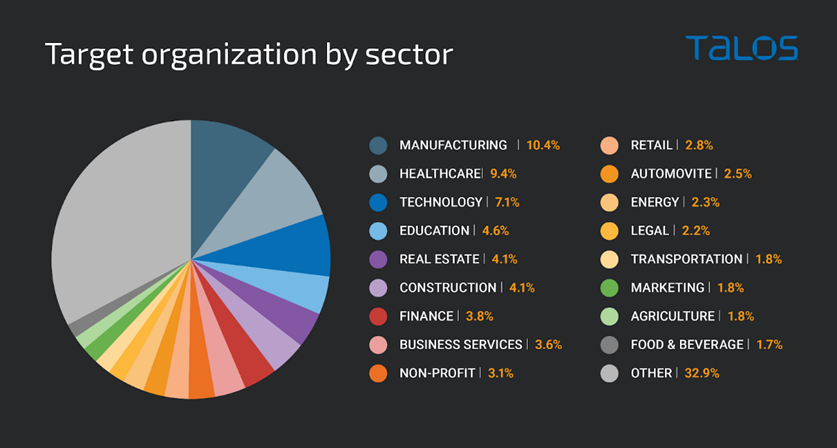
Of the tracked campaigns using this tool, the researchers noted that the most targeted sector was healthcare, followed by manufacturing and technology.
A list of URLs seen used in these campaigns can be found on Cisco’s GitHub repository here.
Phishing attacks are one of the most used methods by hackers to gain access to a system. To reduce the chances of a phishing attack becoming successful:
If you receive a phishing attack in your personal email inbox or on your phone number, you can help stop the campaign by reporting the message. The National Cyber Security Centre has a phishing email reporting system and phishing text message reporting system. Emails can be reported to them by forwarding the message to [email protected], and text messages can be reported by forwarding the message to the number 7726. The NCSC also has advice on what to do if you think you have fallen for a phishing attack, which can be found here.