
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
A new phishing-as-a-service platform called ONNX Store has emerged, posing a severe threat to financial institutions by targeting employees’ Microsoft 365 accounts. Developed by a threat actor known as MRxC0DER, ONNX Store is likely a rebranded version of the Caffeine phishing kit. This service operates through Telegram bots, enabling cyber criminals to orchestrate phishing campaigns and bypass multi-factor authentication (MFA) security measures.
ONNX Store employs a deceptive tactic known as “quishing” (QR code phishing) to lure victims. Cyber criminals distribute malicious PDF attachments via phishing emails impersonating human resources departments or service providers. These PDFs contain embedded QR codes that, when scanned, redirect victims to fake Microsoft 365 login pages controlled by the attackers.
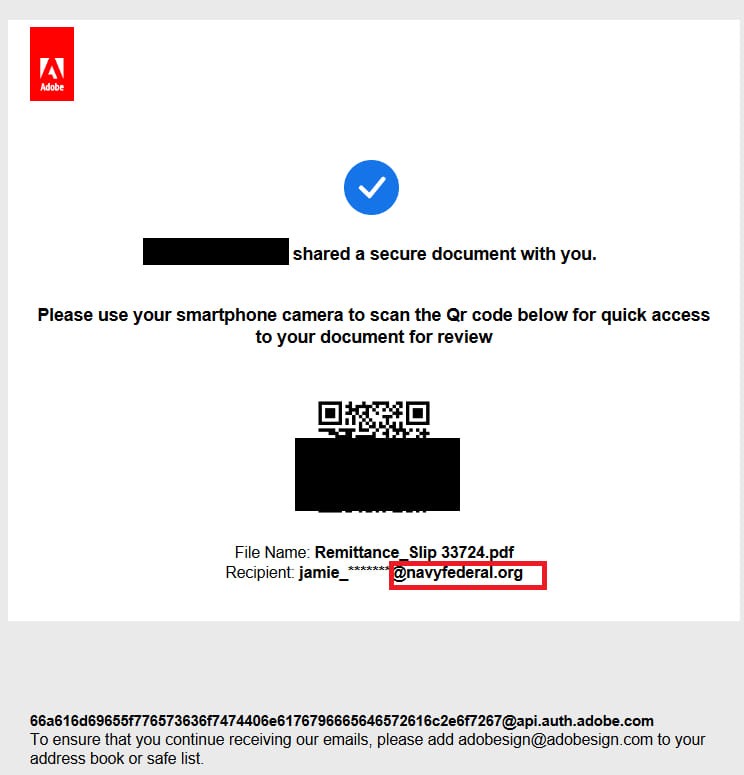
Once on the phishing page, victims are prompted to enter their login credentials and 2FA token. The stolen data is immediately relayed to the attackers via WebSockets, allowing them to hijack the target’s account before the 2FA token expires. This real-time relay of credentials enables the attackers to bypass MFA security.

ONNX Store provides a user-friendly interface for managing phishing operations, including customisable templates, webmail services for sending phishing emails, and bulletproof hosting to evade takedowns. The platform also uses encrypted JavaScript code and Cloudflare services to obfuscate its activities and prevent detection by security tools.
ONNX Store offers various subscription tiers, ranging from $150 to $400 per month, catering to different levels of phishing capabilities, such as webmail services, 2FA bypass, and cookie stealing.

The primary targets of ONNX Store’s phishing campaigns are employees at banks, credit unions, and private funding firms across Europe, the Middle East, and the Americas. Stolen Microsoft 365 credentials can grant attackers access to sensitive information, financial data, and corporate networks, potentially leading to further malicious activities like data exfiltration or ransomware attacks.
To protect against ONNX Store’s sophisticated phishing attacks, organisations should implement the following measures:
If you suspect you have fallen victim to an ONNX Store phishing attack, immediately change your compromised passwords, enable MFA if not already in place, check active sessions, and notify your IT security team or relevant department where you can get support.
Implementing robust security measures, and promoting cyber security awareness, organisations can better protect themselves against the evolving threat posed by the ONNX phishing service and similar malicious platforms.
Additional content on this threat including MITRE and IOCs available at: