
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
Description:
Researchers at Sophos have published research detailing a new malware campaign using Microsoft OneNote documents (also called “Notebooks” by Microsoft) to spread malicious files through phishing attacks. Known as Qakbot, the group has been active since 2008 and spreads banking trojan malware that can steal sensitive information and self-propagate to other systems on the network.
Researchers first saw Qakbot using OneNote documents on January 31st, 2023, when two parallel spam campaigns were observed attempting to spread malware using .one files. One of the spam campaigns used malicious emails with an embedded link, requesting users to download a file containing the Qakbot malware.
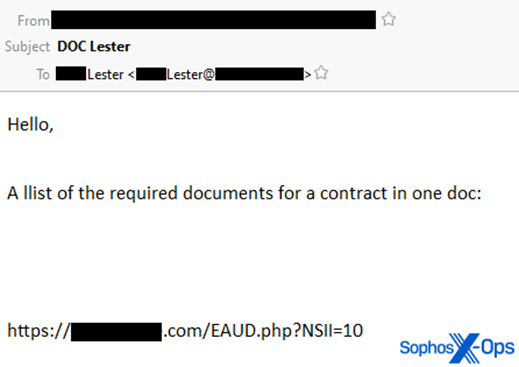
The second campaign involves the threat actors using a compromised email account. They reply to existing email threads with a message asking recipients to open a malicious OneNote file attached to the email urgently.
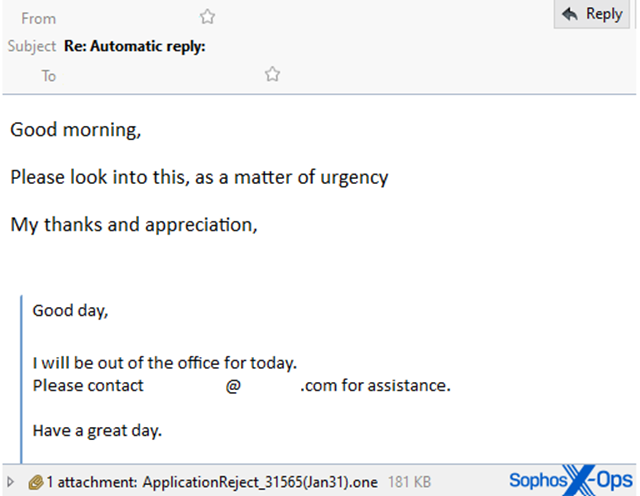
Should a user open the attachment or embedded link from these malicious emails, they will be redirected to a OneNote page asking them to download attachments from the cloud by clicking on a button.
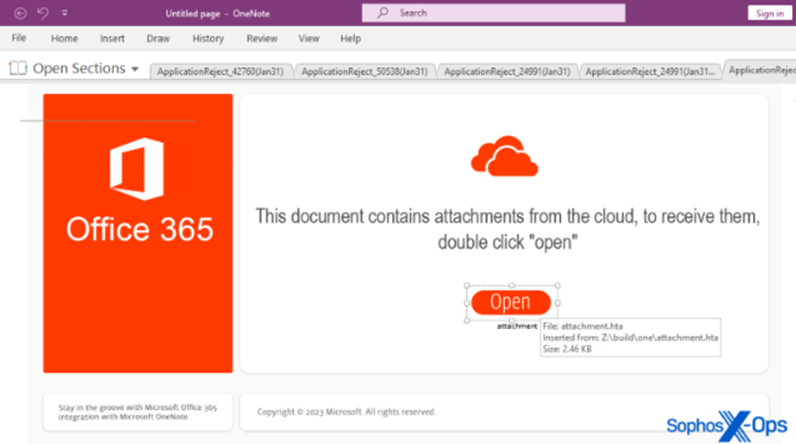
This leads to the Qakbot malware being downloaded from a remote server and executed. It will attempt to steal information such as user credentials, cookies from browsers, and emails stored on the infected machine. Once running, Qakbot injects itself into the Windows Assistive Technology manager to help hide its presence, meaning it may not be immediately detected by an antivirus running on the infected machine. The malware can also be a backdoor to the infected device, allowing threat actors to access and exploit the system further.
The use of OneNote files as an attack vector is possibly due to Microsoft automatically disabling macros in Office documents, meaning an attacker would have to rely on a victim having manually turned on macros to carry out an attack. OneNote allows almost any file type to be embedded within a .one file and only requires a user to double-click on the embedded attachment to run.
It should be noted that Qakbot is often seen targeting financial institutions and has been used to help threat actors commit financial fraud and identity theft by stealing sensitive banking and financial information. Researchers at Sophos noted that this method has allowed the Qakbot campaign to run in a highly streamlined and automated fashion.
Preventions:
To protect your organisation from being attacked, it is highly recommended to block emails containing OneNote (.one) files, especially if members of your organisation do not regularly use OneNote.
Putting measures in place to protect against malicious files will help protect against Qakbot, as well as all forms of malware:
Additionally, protecting your organisation’s email accounts from receiving phishing attacks will help protect users from receiving targeted Qakbot attacks. The following steps can help prevent phishing attacks:
Sophos has provided indicators of compromise (IoCs) from their observed Qakbot attacks, which can be found here. These include URLs, IP addresses, and file hashes. Blocking these IoCs on your firewall and antivirus systems can help them detect and prevent a Qakbot attack.
It is also highly recommended that financial institutions warn staff members of the Qakbot attacks, such as by showing them the types of phishing emails sent by Qakbot. This can help keep staff aware of attacks happening to other organisations within the financial industry.
Related Links:
https://news.sophos.com/en-us/2023/02/06/qakbot-onenote-attacks/ – Published February 6th
https://www.bleepingcomputer.com/news/security/new-qaknote-attacks-push-qbot-malware-via-microsoft-onenote-files/ – Published February 7th
https://blog.cyble.com/2023/02/01/qakbots-evolution-continues-with-new-strategies/ – Published February 1st