
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
Description:
In September 2022, Sophos released a security advisory warning of a critical remote code execution vulnerability that had been seen exploited in the wild. Although a patch for the bug alongside the advisory, researchers have recently found that there are at least 4,000 internet-facing firewalls that have not yet been patched.
Researchers at VulnCheck have released an article detailing how internet scans were used to identify firewalls running versions that had a hotfix available, as well as ones running versions still vulnerable to the bug, tracked as CVE-2022-3236.
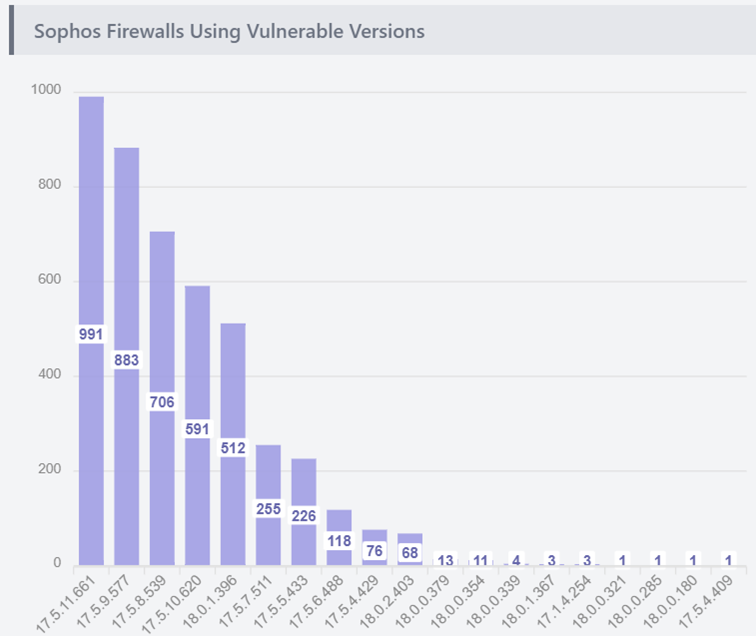
The vulnerability identified by Sophos in 2022 is classed as being of critical severity, as a threat actor would not require privileges or user interaction to carry out an attack, which is described as being of low complexity to do.
VulnCheck researchers have encouraged Sophos Firewall administrators to check firewall logs for indicators of exploit attempts for the vulnerability. They have noted that the files ‘/log/validationError.log.’ and ‘/logs/csc.log’ should especially be focused on.
It is highly recommended for organisations using a Sophos Firewall to ensure that they have updated their firewall to the latest version. The vulnerability affects versions v19.0 MR1 (19.0.1) and older.
If you cannot update your firewall, Sophos has advised that the best workaround is ensuring the User Portal and Webadmin interfaces are not exposed to a WAN. However, this only protects against external attackers and does not totally resolve the issue.
Related Links:
https://www.theregister.com/2023/01/18/4000_buggy_sophos_firewalls/ – Published January 18th
https://vulncheck.com/blog/sophos-cve-2022-3236 – Published January 13th