
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
Researchers at Sansec, an e-commerce malware and vulnerability detection organisation, have warned businesses using the open-source Adobe Commerce/Magento e-commerce platform that they have seen a significant rise in TrojanOrder attacks on the platform in recent weeks. Their report shows a substantial increase in attacks during October, with the number of attacks in November predicted to be more than the entire year combined.
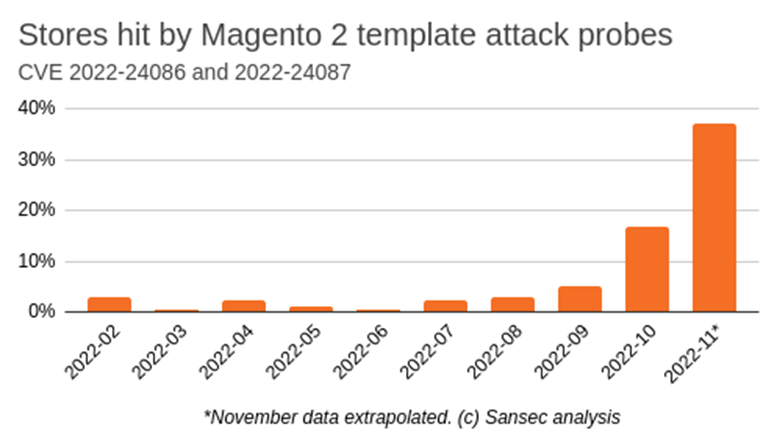
The attacks detected by Sansec exploit the mail template vulnerability (CVE-2022-24086) in Magento 2. The vulnerability was first addressed by Adobe in February 2022 and given a critical severity rating due to its low attack complexity and the no user interaction needed for an exploit to be successful. Despite patches for the vulnerability being released by Adobe in February 2022, Sansec estimates that around a third of all Magento and Adobe Commerce stores have not yet been patched.
To exploit the attack, researchers detailed that threat actors first try to trigger the system to send an email containing exploit code to the server hosting the website. Sending a malicious email can be activated in several ways, including placing an order, signing up as a customer, or sharing a wish list. If the email is successful, the attacker can take over the website.
With access to the site, Sansec has typically seen threat actors establish prolonged access to the host by installing a remote access trojan. This allows the hackers access even after the website has been patched or upgraded. Reporters noted that the trojan is often seen hidden in the file health_check.php, a typically legitimate Magento component. Sansec has previously released a more detailed article that includes exploiting code for several attack templates, which can be read here.
At the time of writing, Sansec has detected seven different attack vectors exploiting this vulnerability, indicating at least seven threat actor groups are now actively attacking vulnerable Magento websites. The researchers have also seen an increase in active scanning for the file that contains the backdoor, health_check.php, indicating that attacker groups are attempting to gain access to sites already compromised by other attackers.
The rise in attacks may be due to an increase in low-cost exploit kits that are easy for hackers to use. The timing also coincides with the rise in online shopping seen during the holiday season, especially around Black Friday and Cyber Monday. The high number of orders many e-commerce sites experience during this period means that attacks are less likely to be noticed or investigated.
Sansec warns that most Magento and Adobe Commerce websites were exposed to this vulnerability before patches were released in February 2022. They warn that there is a chance some sites have already been attacked and have had a backdoor installed. Even if your site has been updated to the latest version since February 2022, a backdoor will still allow attackers access to your system. The backdoors are typically well hidden but can be detected with backend malware scanners.
Preventions:
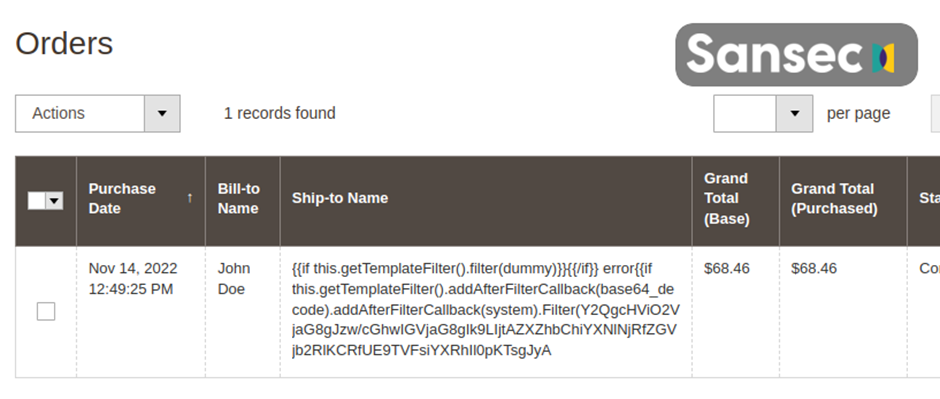
Sansec has identified that the first visible sign of many attacks are suspicious new customer records or transactions. New customers with names or addresses that include “system” or “pwd” may indicate your site is being probed. Orders from anonymous email accounts, such as Protonmail or Tutanota, may also signify an attempted attack.
The best way to protect your website is to apply the patches for the vulnerabilities as soon as possible or update your website to the latest version of Adobe Commerce/Magento. Adobe’s security bulletin addresses the mail template vulnerability in Adobe Commerce and Magento and links to the security updates.
Sansec has previously published an article containing other forms of exploit code and some IPs involved in the attacks, which can be found here. If you cannot apply the updates that patch the vulnerability allowing for these attacks, blocking any known malicious IP addresses from accessing your website and setting detection systems to alert you of new orders containing exploit code may help prevent you from becoming victim to these attacks.
As some sites may have been infected before security updates became available, using a backend malware scanner is recommended to discover if a potential past infection has resulted in a remote access trojan or other malware being downloaded within your system.
Related Links:
https://sansec.io/research/trojanorder-magento – Published 15th November
https://www.bleepingcomputer.com/news/security/magento-stores-targeted-in-massive-surge-of-trojanorders-attacks/ – Published 16th November
https://sansec.io/research/magento-2-template-attacks – Published 22nd September 2022