
Data Privacy Starts With Cyber Basics
Data Privacy Day is a useful reminder that privacy and cyber security are not separate conversations. You can have the best privacy policy in the…
Malware loaders are rising as a cyber security threat, with new and dangerous variations emerging constantly. While the technical details may be complex, the public needs to understand these cybercriminal tools. Knowing malware loader techniques can help individuals and organisations avoid becoming victims.
In simple terms, malware loaders are hacker tools used to install malicious software onto a computer or network secretly. Their primary purpose is to bypass antivirus defences and other security measures to deliver a malware payload.
Some of the most common types of malware spread by loaders include remote access Trojans, keyloggers, spyware, adware, ransomware and more. Once installed, this malware allows hackers to steal data, encrypt files for ransom, monitor activities and more.
Malware loaders use a variety of clever tricks to avoid detection. For example, some loaders exploit vulnerabilities in popular software like web browsers and apps. This allows them to sneak past security defences.
Other loaders utilise encryption to scramble their code and conceal malware payloads from antivirus scans. Some are built using modular components to disguise their intentions. Still, others spread through phishing emails and infected ads and sites.
By leveraging these techniques, malware loaders can infiltrate networks and endpoints while evading traditional safeguards. This enables them to download even more harmful threats directly onto targets.
While there are many loader variants, researchers at ReliaQuest have found seven main loaders used in attacks today.
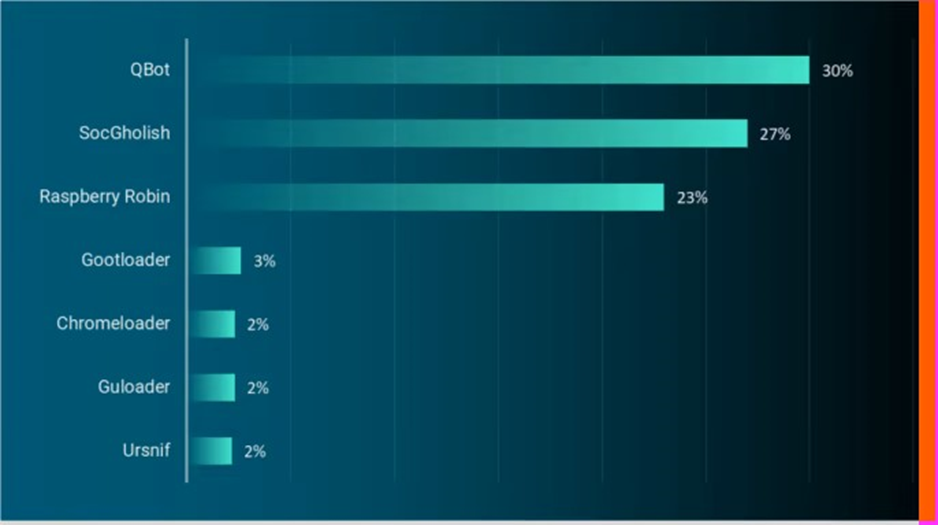
Above are the seven most used loaders found in customer environments. These loaders should be highlighted to individuals and organisations as something you want to protect against.
“QakBot” “SocGholish,” and “Raspberry Robin” were overwhelmingly the most popular loaders. This accounted for 80% of incidents involving malware loaders that ReliaQuest observed.
While malware loaders present a severe threat, there are ways to improve protection:
Staying vigilant against the latest malware loader tactics can prevent cybercriminals from gaining a foothold in your network. Individuals and businesses can guard against these threats with awareness and proper security.