
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
The NSO Group, which was founded in 2010, produces and sells “Cyber Warfare” mobile phone spyware suite called Pegasus. On their website they state their technology is to help “government agencies prevent and investigate terrorism and crime to save thousands of lives around the globe”, however, due to a recent leak of their data their claims may turn out to be false (1).
The NSO Group is known as a surveillance vendor and sells their services to governments worldwide, stating that their “precision cyber intelligence solutions (is) for the sole use of vetted-and-approved, state-administered intelligence and law enforcement agencies”.
NSO Group’s malware is installed by either tricking a target to click on a malicious link or exploiting an unknown security vulnerability in well-known apps. Once Pegasus is installed on to a victim’s Android or iPhone device, the harvesting of private data begins. This includes all messages from Signal, WhatsApp, Telegram, emails, contact information and being able to activate the phone’s camera and microphone which can capture activity in the phone’s vicinity.
This spyware can essentially engulf all your private information, your personal interactions and create a grid of the people you know, the places you have been all without knowledge of being surveilled and relaying all your private data to whomever paid for the NSO’s Group services.
A target has to click on a “specially crafted exploit link” which then delivers a “chain of zero-day exploits”. These exploits penetrate security features on the target’s device and is the attack vector enabling Pegasus to be installed, in stealth, without consent or knowledge of the target.
Citizen Lab’s research on Pegasus has shown that once the malware is installed “it begins contacting the operator’s command and control (C&C) servers to receive and execute operators’ commands” which then sends back the victims private data ranging from text messages to passwords and contact lists as well as live voice calls.
“Pegasus exploit links and C&C servers use HTTPS, which requires operators to register and maintain domain names. Domain names for exploit links sometimes impersonate mobile providers, online services, banks, and government services, which may make the links appear to be benign at first glance. An operator may have several domain names that they use in exploit links they send, and also have several domain names they use for C&C. The domain names often resolve to cloud-based virtual private servers (front-end servers) rented either by NSO Group or the operator. The front-end servers appear to forward traffic (via a chain of other servers) to servers located on the operator’s premises (back-end Pegasus servers).” (3)
Report from Citizen Lab.
A forensic analysis of infected devices determined that the use of “zero-click” exploits which did not require the target to interact were in operation. This also indicates the technical advancement of NSO who would have previously been utilising “spear-phishing attacks” for targets to click on malicious links. Using “zero-click” exploits also makes it more difficult for the target to notice or even be suspicious of the Pegasus spyware. The NSO Group has “leveraged multiple zero-days in iMessage to attack a fully patched iPhone 12 running iOS 14.6 in July 2021” indicating they can hack into the latest iPhones unimpeded. This also highlights a security issue with iMessage that BlastDoor Framework has not been able to resolve.

WhatsApp identified that over 1,400 phones had been exploited by a zero-day vulnerability enabling the NSO software to deliver its malware. Malicious Pegasus code could be installed through placing a WhatsApp call to a victim’s device, even if they never answered the call. This was discovered in 2019. NSO continuous its exploitations of vulnerabilities of Apple software, creating back-doors in iPhones which can target millions of Apple’s customers. Once the iPhone has been compromised, root privileges are obtained and “Pegasus can do more than what the owner of the device can do”.
A large-scale data leak of over 50,000 phone numbers going back to 2016, indicating selected “persons of interest by government clients of NSO Group” has just been revealed. Amnesty International and Forbidden Stories, a non-profit journalism organisation had original access to this list who proceeded to share this information with other media organisations.
NSO Group’s clients include government officials, religious figures, academics, union officials, NGO employees and business executives and spanned many countries including “Azerbaijan, Bahrain, Hungary, India, Kazakhstan, Mexico, Morocco, Rwanda, Saudi Arabia, Togo, and the U.A.E.”. Spanning from 2014 up until 2021. Countries like Hungary, Rwanda, Morocco, and India are denying ever using Pegasus to hack any individuals.
NSO claims its spyware is only for legitimate use.
In the last few days, the world has rightly been outraged by the systematic targeting of human rights activists, journalists and lawyers revealed by the Pegasus Project. Not only does it expose the risk and harm to those individuals unlawfully targeted, but also the extremely destabilizing consequences on global human rights and the security of the digital environment at large.
Agnes Callamard, Amnesty International’s Secretary General.
Citizen Lab’s research into NSO Pegasus infections spanned 45 different countries.
Combined with the findings from Citizen Lab and the data leak it is indicative of “widespread and continuing abuse” of NSO’s spyware. This brings up serious issues that surveillance malware is being sold to governments around the world which hold massive ethical implications and human right issues which are the tip of the iceberg.
The problems arise when powerful spyware is created by a private company, which would not necessarily be held to the same levels of accountability or scrutiny elsewhere. This also creates a new industry for stealth cyber warfare where there are no boundaries or limitations towards targeted individuals’ personal devices to be turned into round the clock surveillance. It also has the capability to infect any phone, which means billions of people are vulnerable to this spyware.
Malware for-profit companies are legitimising criminal activity that if that industry goes unchecked, opens the door to the potential of the dissolution of democracy and governments losing credibility from their citizens.
Having few legally enforced protocols for this industry does not bode well for the future. With no vetting, no regulation and not going through proper credible and legitimate processes of surveillance, no individual, no companies, no industries, and no countries will be protected from being a potential target.
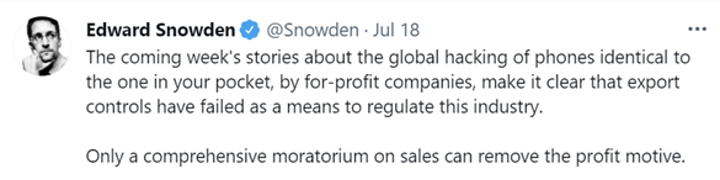
Edward Snowden calls for a ban on spyware trade, if “no phone is safe from state-sponsored hackers” and no action is taken to curb this, the outcomes could be paradigm shifting.
NSO. NSO. [Online] 2021. [Cited: 20 07 2021.] https://www.nsogroup.com/.
New Leak Reveals Abuse of Pegasus. The Hacker News. [Online] 18 07 2021. [Cited: 20 07 2021.] https://thehackernews.com/2021/07/new-leak-reveals-abuse-of-pegasus.html.
Tracking NSO Groups Pegasus Spyware. Citizen Lab. [Online] 18 09 2018. [Cited: 20 07 2021.] https://citizenlab.ca/2018/09/hide-and-seek-tracking-nso-groups-pegasus-spyware-to-operations-in-45-countries/.
What is Pegasus Spyware and How Does it Hack Phones. The Guardian . [Online] 18 07 2021. [Cited: 20 07 2021.] https://www.theguardian.com/news/2021/jul/18/what-is-pegasus-spyware-and-how-does-it-hack-phones.
Snowden. Twitter. [Online] 18 07 2021. [Cited: 20 07 2021.] https://twitter.com/Snowden/status/1416808958594015233.