
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
Description:
Researchers at FortiGuard Labs have recently published a report detailing a new botnet, named GoTrim, seen scanning the web for self-hosted WordPress websites and using compromised credentials to attempt to gain access to the site’s administrator account. The earliest botnet samples were seen in September 2022 and are still active at the time of writing.
To attack WordPress websites, the threat actors behind GoTrim give each bot a set of credentials and a long list of websites to attack. If a bot successfully logs in, a bot client is installed into the compromised system and awaits further commands from the threat actors. This bot client allows the threat actors to expand their botnet, giving them more computing power to attack more websites. The researchers observed the botnet only targeting sites hosted on Linux systems.
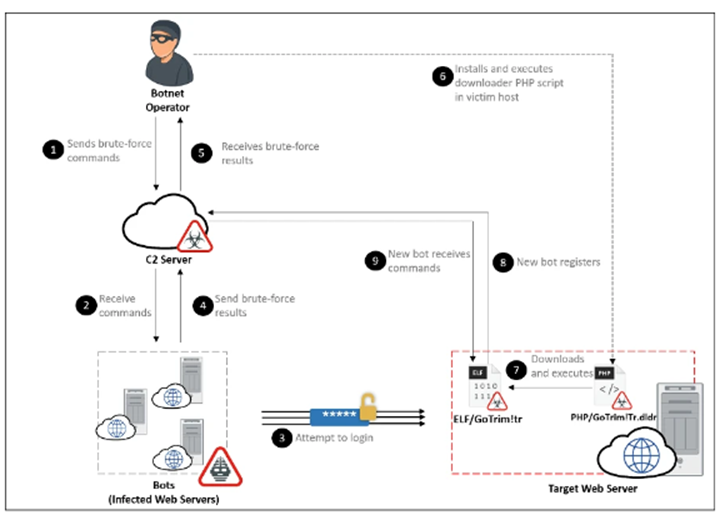
The botnet’s code is written in Go, a programming language popular among malware developers. To communicate with the threat actors, the malware either sends HTTP POST requests to the threat actor’s command and control (C2) server or sets up a HTTP server on the compromised device to listen for incoming POST requests. By default, the malware sets up a server within the compromised device if the device is directly connected to the internet (if the victim’s IP address is non-private). If successful, the malware registers itself as a new bot on the GoTrim botnet.
GoTrim can detect anti-bot techniques typically used by web hosting providers and is built to evade some of the more straightforward checks. To do this, the botnet attempts to mimic legitimate requests from Mozilla Firefox by using the same HTTP headers as the browser, alongside supporting the same encoding algorithms. Additionally, the malware can detect whether CAPTCHA plugins are installed. The researchers noted that although the malware contains code that can solve CAPTCHA requests, they are still verifying if the bot’s bypass techniques work.
Since the discovery of this botnet in September 2022, researchers have identified several malware updates, suggesting that this botnet is still under development.
Protections:
The GoTrim botnet uses brute force as its primary attack technique, which involves the attackers submitting numerous passwords with the hopes of eventually guessing correctly. The best way to protect against attacks like these is to ensure you use strong passwords and different passwords for every account you create.
To create a strong password, we recommend using three random words, along with some numbers and a unique character.
Other protections you can use to protect against brute force attacks are:
The researchers at FortiGuard Labs have provided indicators of compromise of this attack, which can be found at the bottom of their report on the botnet. Add these indicators to your detection systems, so you know when a possible attack from this botnet is occurring. You can also protect your systems by blocking the IP addresses and URLs used in this attack.
Related Links: