
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
In recent years, Booking.com, a popular online travel agency, has been the target of several phishing scams. These scams have resulted in significant financial losses for Booking.com, hoteliers and its customers. In recent months, these types of scams have been on the rise again, with
In a typical Booking.com phishing scam, attackers will first gain access to the computer systems of a hotel or BnB. They do this by socially engineering staff into opening a file containing malware; you can see the tactic used in the example emails below. In a recent incident reported in Edinburgh, the threat actors advised the hotel their child had particular dietary/allergy requirements. They stated it was easier to email over the list of their requirements and sent over a file containing the malware, which was opened.
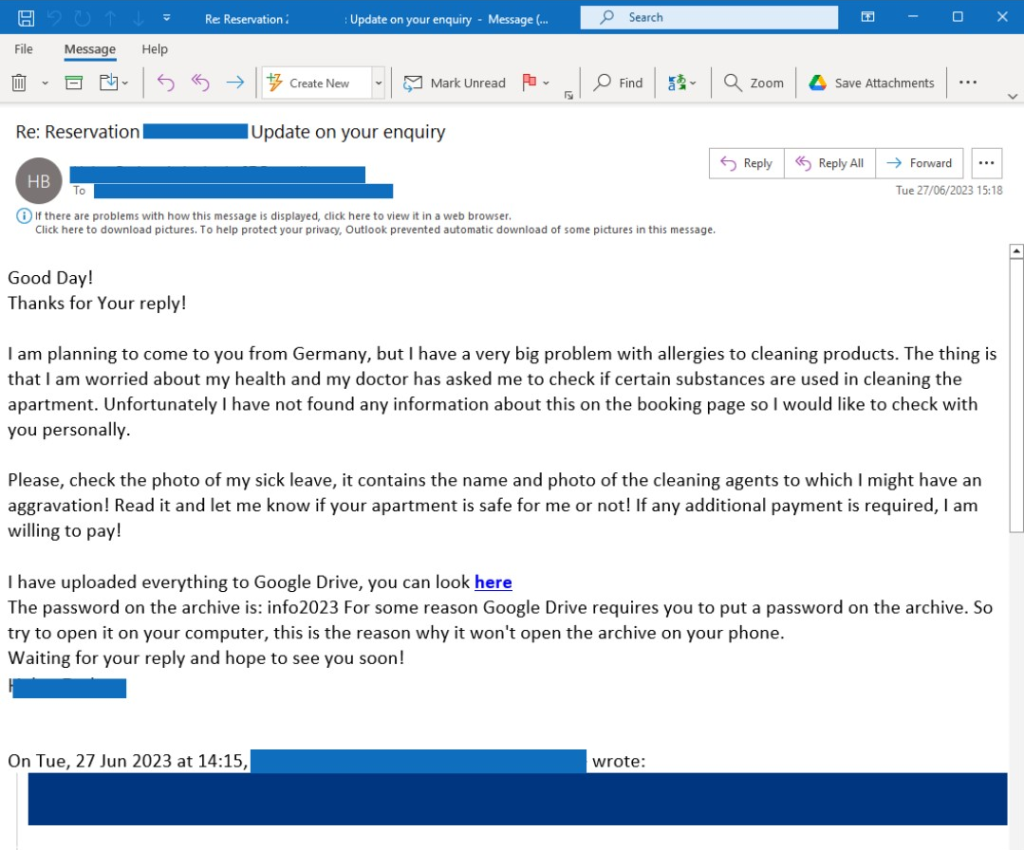
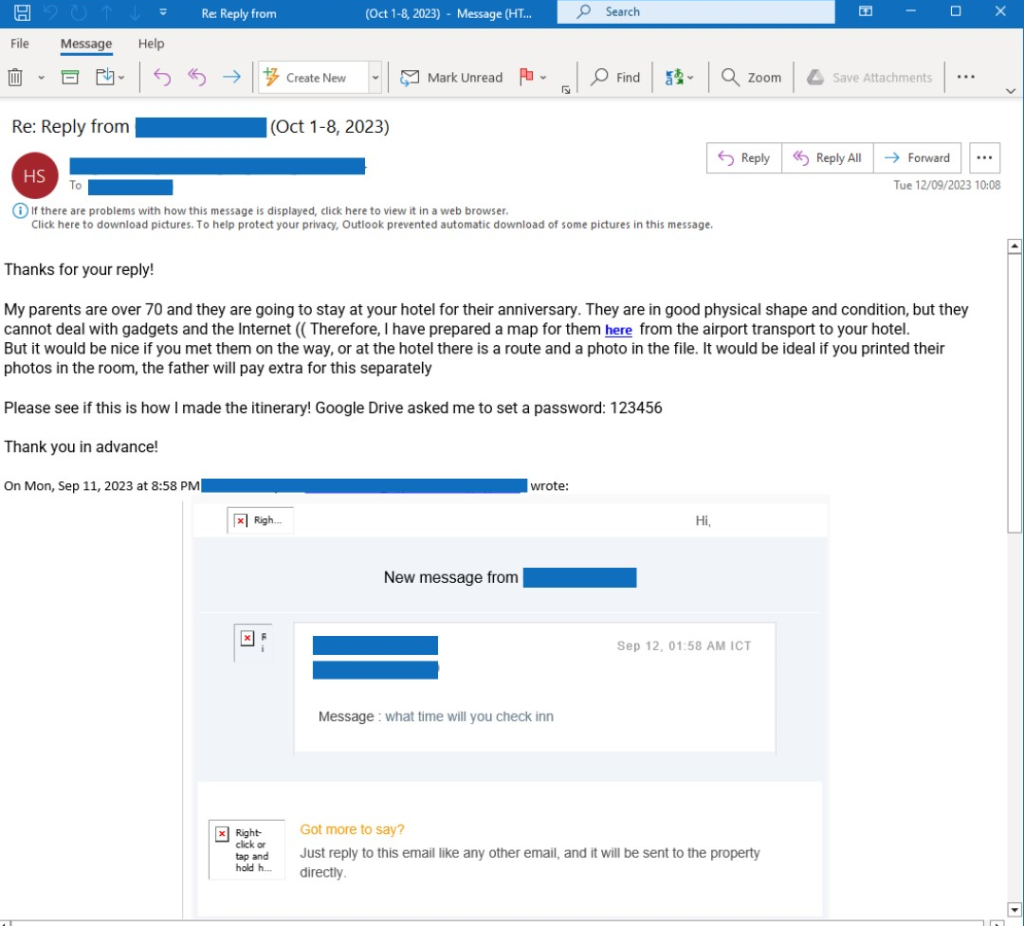
They will then use this access to steal customer data, such as names, email addresses, and credit card numbers.
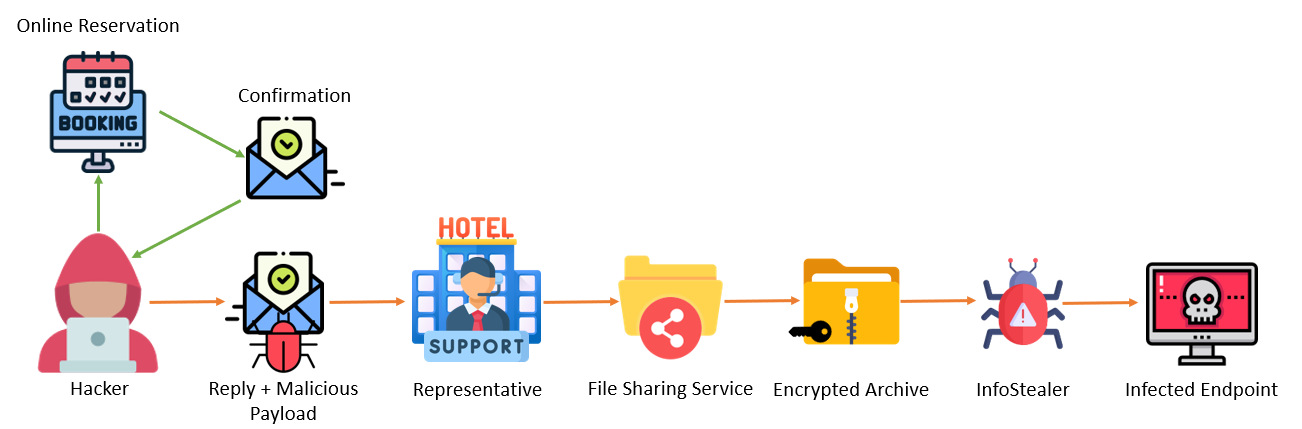
Perception Point, who have reported on this, has identified 10 Steps the hackers take throughout this scam, which are listed below.
With this stolen data, attackers will send phishing emails to Booking.com customers. These emails will often appear to be from Booking.com itself and often contain urgent requests or enticing offers. For example, recent emails have advised customers they are required to carry out additional card confirmations or that the booking could be cancelled if they didn’t verify their payment method.
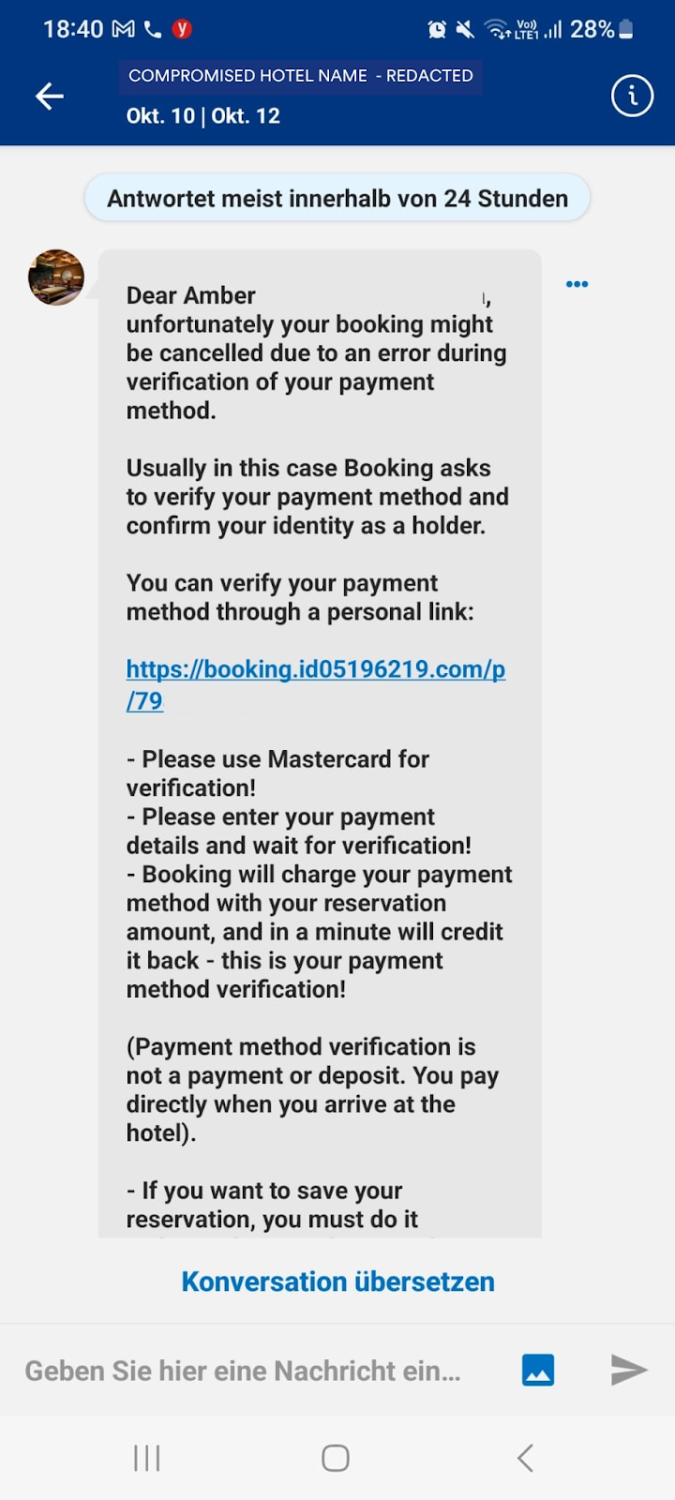
The phishing emails will typically contain links to fake Booking.com websites. When a customer clicks on one of these links, they will be taken to a website that looks similar to the actual Booking.com website. However, the fake website is controlled by the attackers.
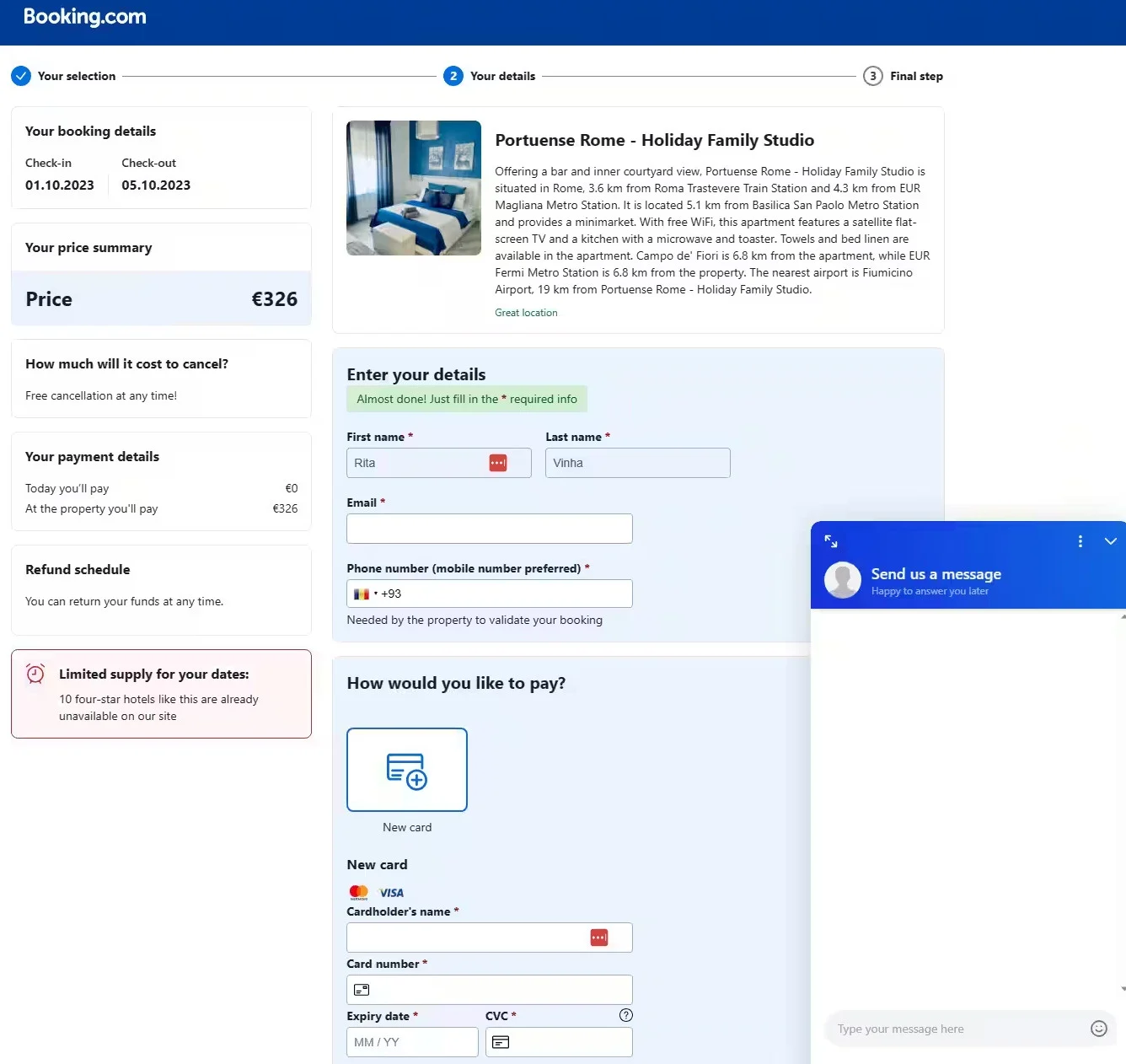
Fake Booking.com example – customers are completing these, unaware of the scam
Once a customer enters their personal information on the fake website, the attackers will steal it. They can then use this information to make unauthorised purchases or to commit further crimes, including identity theft.
The Booking.com phishing scams have significantly impacted Booking.com, its customers and the associated hotels and bed and breakfast owners who use booking.com to generate business. Booking.com has damaged its reputation and has had to spend money to investigate and remediate the attacks. Customers have suffered financial losses and had their personal information stolen, and hotels report that directly from these crimes. Customers have been cancelling bookings and events as they do not know if they will be reimbursed. Hotels have also had to go through the process of purchasing new computer equipment or hiring specialist cyber security specialists to ensure their systems are free from malware.
There are several things that you can do to protect yourself from Booking.com phishing scams:
Booking.com phishing scams are a severe threat to Booking.com, hoteliers and its customers. However, following the tips above, you can protect yourself from these scams.