
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
Affected Systems:
Description:
Fortinet has released a security advisory warning users of an authentication bypass vulnerability affecting its firewall and proxy products. The vulnerability, tracked as CVE-2022-40684, has a critical severity rating and has been seen actively exploited by hackers.
Alongside being announced in Fortinet’s advisory, the vulnerability has also been added to The U.S. Cybersecurity and Infrastructure Security Agency’s (CISA) Known Exploited Vulnerabilities Catalogue on October 11th.
The vulnerability is exploited using specially crafted HTTP and HTTPS requests. If successful, hackers can bypass authentication and remotely access the compromised product’s administrative interface. This access allows them to disable or override administrator functions, meaning hackers can configure the firewall or proxy of an organisation to allow for a further compromise into the network.
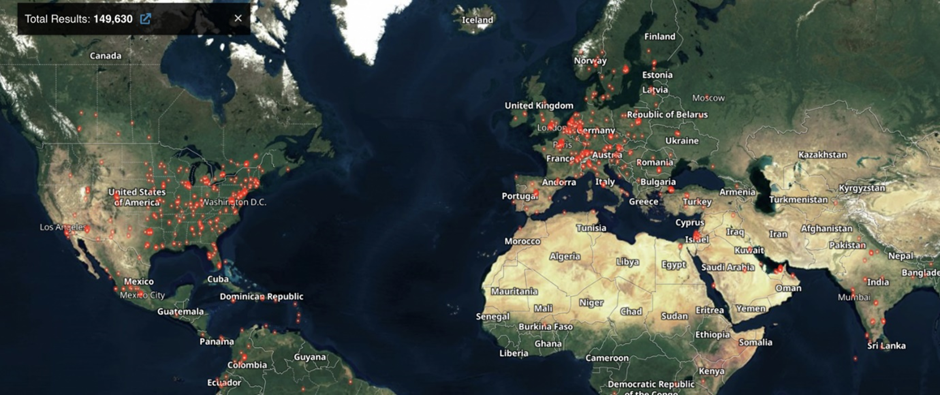
Horizon3.ai’s chief attack engineer Zach Hanley has told BleepingComputer that “Vulnerabilities affecting devices on the edge of corporate networks are among the most sought after by threat actors because it leads to breaching the perimeter, and CVE-2022-40684 allows exactly this” BleepingComputer has found that over 140,000 FortiGate firewalls are exposed on the internet, and could be vulnerable to attacks if their admin management interfaces are also exposed.
Preventions:
Fortinet has released updates for affected versions, asking customers to update their products as follows:
As this vulnerability is being actively exploited, Fortinet has recommended checking for the following string in your device’s logs:
user=” Local_Process_Access”
If this string is in your logs, it could indicate that your device has been compromised.
Security researchers at Hotizon3.ai have shared some more indicators of compromise alongside a technical explanation for this vulnerability, which can be found here.
If you cannot update your systems, Fortinet has included workarounds to protect against attackers exploiting this bug in their security advisory.
All affected products (FortiProxy, FortiSwitchManager, and FortiOS) can disable the HTTP/HTTPS administrative interface as a workaround.
FortiOS and FortiProxy can also limit the IP addresses that can reach the administrative interfaces to prevent unauthorized access. Fortinet has provided the commands to do so in its security advisory.
Related Links:
https://www.fortiguard.com/psirt/FG-IR-22-377 – Published October 10th
https://www.cisa.gov/uscert/ncas/current-activity/2022/10/11/cisa-has-added-one-known-exploited-vulnerability-catalog – Published October 11th
https://thehackernews.com/2022/10/fortinet-warns-of-active-exploitation.html – Posted October 11th
https://www.horizon3.ai/fortinet-iocs-cve-2022-40684/ – Published October 11th