
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
Researchers at Fortinet’s FortiGuard labs have published an article detailing their observations of a new LockBit ransomware campaign.
The LockBit ransomware campaign has been active since September 2019. It operates using the Ransomware as a Service (RaaS) model, meaning threat actors can rent out the malware for personal use. This model has allowed for Lockbit to be continuously updated, and there have been three new versions of the malware since 2019, the most recent being Lockbit 3.0. The new campaign observed at FortiGuard has seen LockBit using several techniques to evade detection and persist within an organisation’s network.
Beginning in December 2022, the recently observed attacks used an image file containing hidden malicious files. These malicious files are run once the main image file is downloaded, and first check for the privilege level of the user who downloaded the file. In some cases, the program attempted to elevate the privileges of this user. Then, the user’s password is changed, and the system is rebooted, executing the ransomware once the device starts back up.
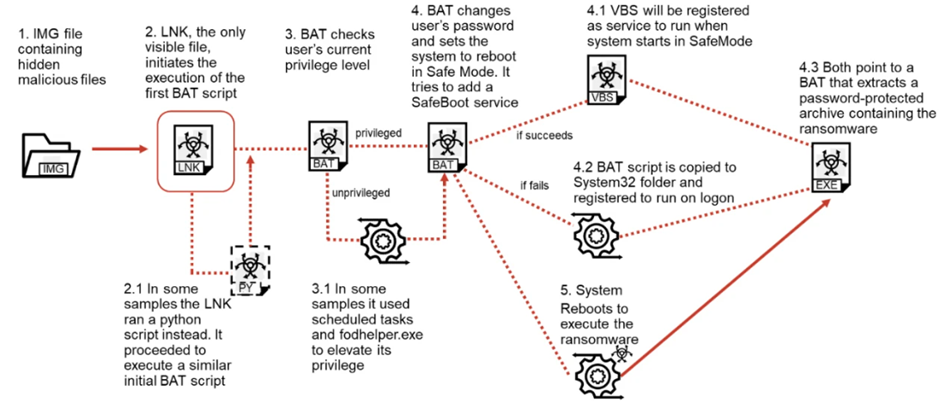
The researchers especially highlighted Lockbit’s ability to avoid detection from anti-viruses and other defence mechanisms. When tested on VirusTotal, security vendors consistently missed the samples as being malicious. This is due to multiple methods used by LockBit, such as using multiple stages to set up the compromised device and configuring the device to run the ransomware script without requiring any user interaction.
Other versions of LockBit include other methods to evade detection. These include using hidden windows to hide the activity of malicious scripts as they run, disabling Windows Defender and other anti-virus solutions (if the compromised user’s permissions allow for it), and deleting event logs and other indicators off of the infected device.
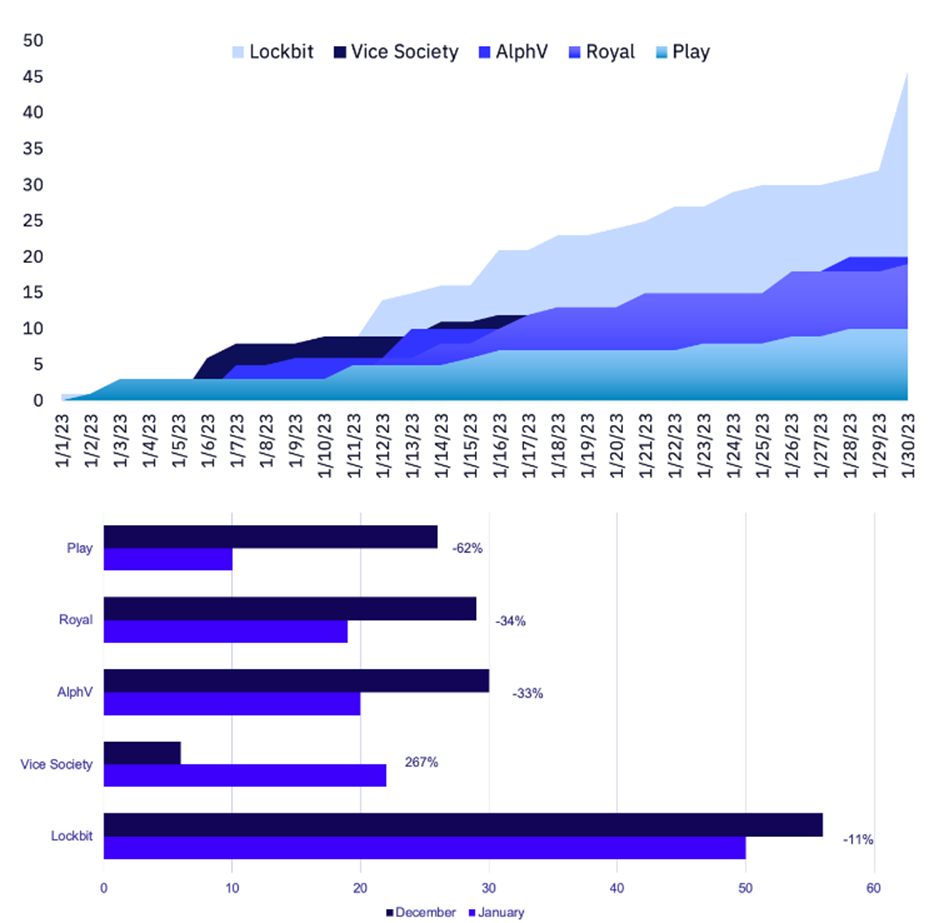
These evasion techniques have proved highly successful through recent attacks on large organisations, such as the attack on Royal Mail’s international mail services. In January 2023, 31% of all reported ransomware attacks were made by Lockbit, affecting organisations across 23 countries.
Lockbit’s creators are constantly looking to improve their abilities to escape detection and cause destruction. Because of this, protecting against Lockbit ransomware requires more than just anti-virus, but having multiple protection methods to prevent an attack. Some of the best steps to stay protected include:
https://www.fortinet.com/blog/threat-research/emerging-lockbit-campaign – Published 1st March