
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
The trojan malware known as LokiBot or Loki PWS has been identified as a significant threat primarily targeting Windows operating systems. Recent reports indicate that this malware has been disseminated through Microsoft Word files, utilising remote code execution techniques to exploit known vulnerabilities present within the software.
The primary objective of these Word documents is to secretly download an enclosed XML file, which subsequently initiates the delivery of an HTML file. This HTML file, in turn, exploits the Word vulnerabilities, ultimately facilitating the deployment of the LokiBot injector, which is based on the Visual Basic programming language. Security researchers have also uncovered a second attack chain that launches a Visual Basic script and macro upon opening the document.
The intended purpose of this malicious campaign is to collect sensitive information from the infected machines secretively. Given these developments, it is essential to exercise utmost caution when handling Word files, especially from unfamiliar sources, to mitigate the risk of falling victim to this harmful malware.
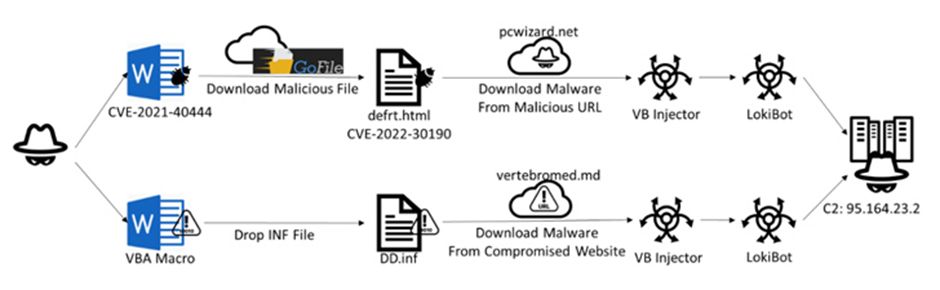
LokiBot is equipped with a range of harmful functionalities, including keylogging, screen capturing, data harvesting, and authentication theft. These capabilities illustrate the malicious nature of the trojan and emphasise the importance of exercising caution when handling email attachments and similar files.
Moreover, researchers have observed that once the malware is delivered, it employs obscure techniques to evade user and antivirus software detection. As such, it is crucial to remain vigilant and take necessary precautions to protect against this sophisticated threat.
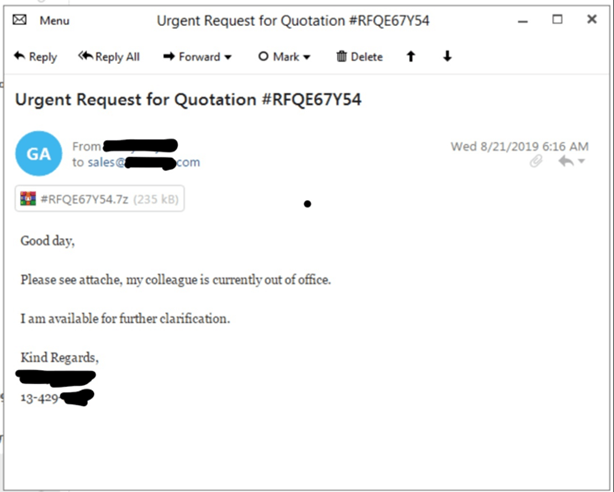
There are a few ways in which you can help reduce the possibility of being infected by malware like Lokibot:
If you receive a phishing message via email or text, you can report them to the National Cyber Security Centre’s phishing report system.
You can find advice on phishing scams, how to spot phishing attacks, and how to report them below: