
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
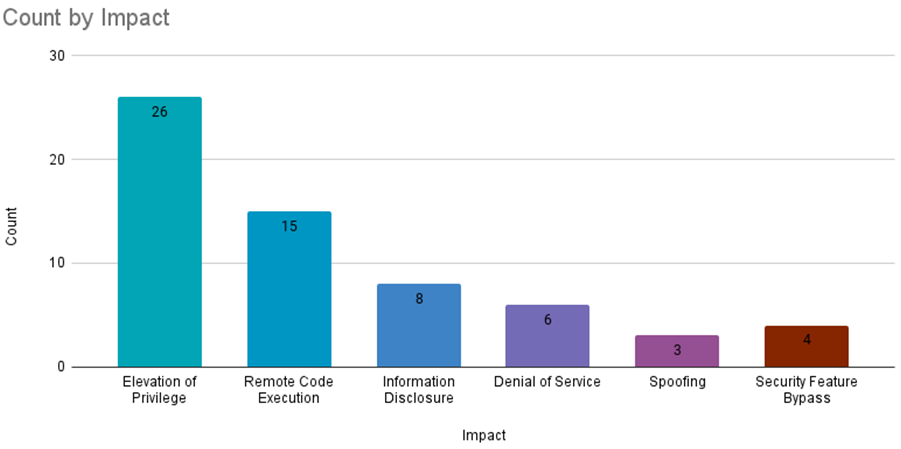
Microsoft’s November Patch Tuesday addresses 62 vulnerabilities, nine of which are critical. Six of the vulnerabilities are actively exploited zero-days, which includes two used in ProxyNotShell attacks (CVE-2022-41082 and CVE-2022-41040) affecting on-premise Microsoft Exchange Servers.
The other four actively exploited vulnerabilities include:
Microsoft is urging administrators to patch systems as soon as possible, as threat actors are actively exploiting several of these vulnerabilities.
Microsoft has published a security update guide for this month’s Patch Tuesday, which includes technical descriptions of all vulnerabilities fixed.
Related Links:
https://www.tenable.com/blog/microsofts-november-2022-patch-tuesday-addresses-62-cves-cve-2022-41073 -Published 8th November
https://msrc.microsoft.com/update-guide/releaseNote/2022-Nov – Published 8th November