
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
Description:
Microsoft’s Threat Intelligence Centre (MSTIC) has published the technical methods and activities relating to a Russian group tracked as SEABORGIUM. The blog details how the threat actor has been primarily targeting organisations in NATO countries, mainly in the UK and US, with spear-phishing emails that aim to steal victims’ login credentials.
MSTIC reports that the group has been targeting defence and intelligence consulting companies, non-governmental and intergovernmental organisations, higher education institutions, and individuals with Microsoft consumer email accounts. When targeting individuals, the threat actor sends simple emails containing small talk and referencing a non-existent attachment, waiting for the target to ask for the file before sending a malicious document containing a link to a phishing site.
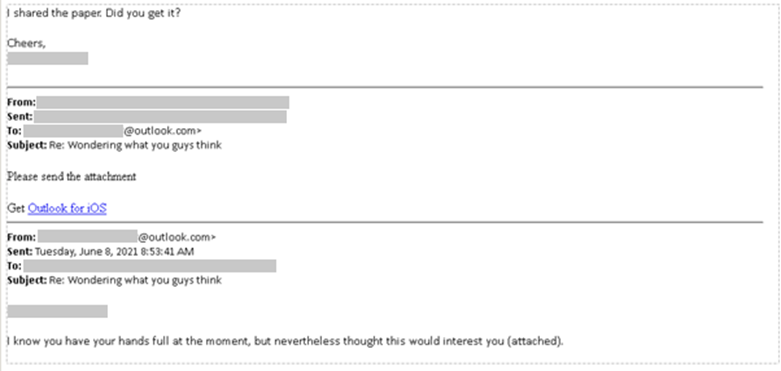
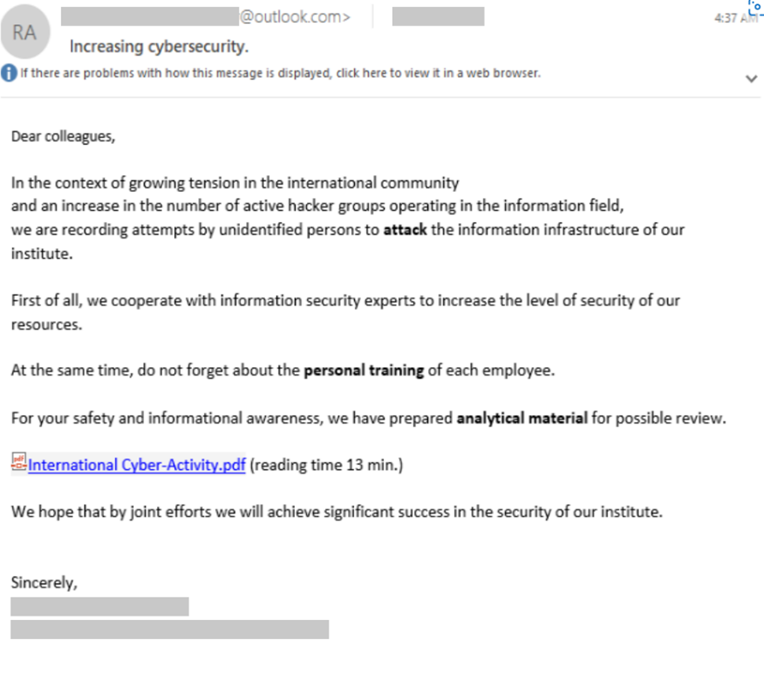
When targeting larger groups or entire organisations, the threat actor will use an “authoritative approach in their social engineering” reports MSTIC, who included an example phishing email showing the threat actor ironically using a cyber security-themed lure to get victims to open a PDF containing a malicious link to their phishing site.
MSTIC noted that the threat actor would often research individuals and organisations before targeting them, using open-source intelligence and social media, such as LinkedIn, to identify contacts in the target’s social network and their sphere of influence in their organisation.
Once SEABORGIUM has successfully stolen a target’s login credentials, they have been observed to directly log into the victim’s email account and then conducting malicious activities, including; exfiltrating data, emails, and attachments from compromised mailboxes, setting up email forwarding rules for long-term data collection and using compromised accounts to contact other people of interest. MSTIC states that espionage may be a key motivation for this threat actor due to their specific victimology and sustained data collection methods.
The full report on SEABORGIUM can be found here.
Preventions:
As this threat actor’s primary method of targeting victims is through phishing attacks, knowing how to detect phishing emails can significantly reduce your chances of becoming a victim. Phishing attacks are one of the most used methods by hackers to gain access to a system.
To minimise the chances of a phishing attack becoming successful, you should:
Microsoft has also recommended that customers check Office 365 email filtering settings to ensure that malicious emails are blocked and configuring Office 365 to disable email auto-forwarding.
MSTIC has included some indicators of compromise (IOCs) for this attack in their blog on this threat actor. These IOCs include several domain names linked to SEABORGIUM attacks. If possible, set up systems to detect any activity relating to these domains and consider investigating your environment for any signs of past activity.
Related Links: