
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
Researchers at ESET have recently advised on a new backdoor called ‘MQsTTang’ attributed to Chinese hacking group Mustang Panda, believed to be part of a continuing campaign first discovered in January 2023.
Confirmed attacks are using MQsTTang are located in Bulgaria, Australia, and likely Taiwan, with evidence, such as decoy file names, which suggest targets in Europe and Asia. Evidence from ESET indicates that this new malware is initially installed through spear-phishing attacks. The malware then uses the MQTT protocol for Command and Control communication rather than the intended use of MQTT, which is IoT communication. The malware provides a shell with minimal add-ons, which is unusual for Mustang Panda, and the use of MQTT for Command and Control makes it resilient to C2 takedowns. Using MQTT, the malware prevents direct communication between the C&C centre and the infected device.
This malware is distributed in a RAR archive with only one executable. The .exe file has nearly always had a name related to diplomacy and passports, such as ‘Officer Passport ministry of Foreign affairs.exe’
When the malware is originally launched, it will give itself a command line argument of 1, incrementing itself every time it is run, with commands being executed as it reaches a specific number, as shown in Figure 1.
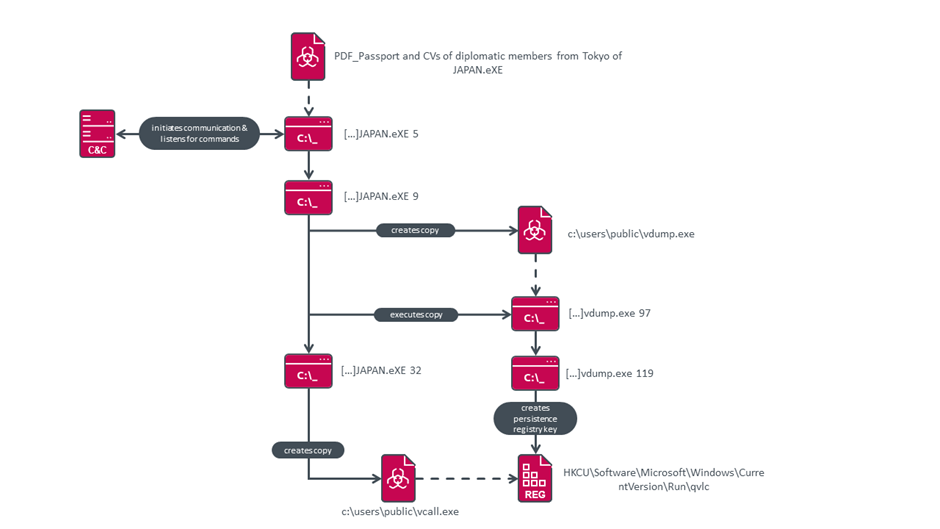
Mustang Panda has targeted government and political organisations with this malware and many other attacks, such as edited versions of PlugX. On top of this, using MQTT is a rarely exploited communication method, making it hard to detect.
Below is advice to mitigate the spread of malware: