
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
Researchers at Mitiga, a cyber security incident response company, have uncovered threat actors targeting senior leaders, such as CEOs and CFOs, with specially crafted spear phishing campaigns along with an Adversary-in-The-Middle (AiTM) attack which allows them to bypass 2-factor authentication (2FA) and create a second authentication method for the hacker to use.
Their report states that the attacks started when an executive within the victim organisation received a phishing email appearing to be from DocuSign, containing a link supposedly to a document that needed to be signed. However, the link instead took the victim to a site used for stealing login credentials and allowing an attacker to steal the authentication cookies created from 2FA logins. The attacker used these stolen cookies to bypass 2FA, and were then able to set up their own separate authentication app for future access to the compromised account.
After compromising the first account, the attackers spent time gathering information about the victim’s organisation and reading emails and files. They then waited for correspondence regarding an upcoming financial transaction and intercepted at the last minute with a fake domain name, asking to change the bank details.
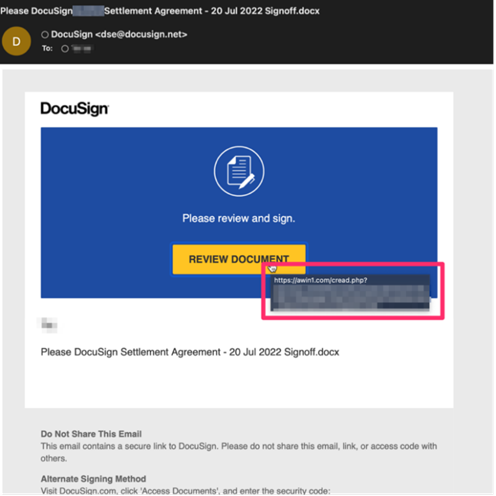
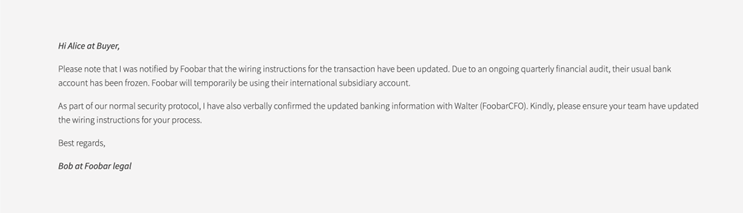
Microsoft is aware of the flaw in its 2FA system and has posted an advisory detailing how such attacks occur. Mitiga has also published an advisory on the attacks using this method that they have monitored.
Preventions:
Mitiga has noted that this type of attack is difficult to prevent, as the threat actors have been taking advantage of Microsoft’s 2FA system. However, they have added that it is possible to add a third layer of defence by only allowing 2FA authenticator apps to exist on a physical device or an employee’s work computer or phone. This can be done on Microsoft 365’s Conditional Access by adding a requirement to authenticate via an enrolled and compliant device only.
Additionally, letting executives and senior positions within your organisation know about this type of attack, as well as the signs of any spear phishing attack, can help prevent your business from becoming a victim.
Mitiga has also posted indicators of compromise for this attack, which include the domain names, email addresses, URLs, and IP addresses of the threat actors conducting this attack.
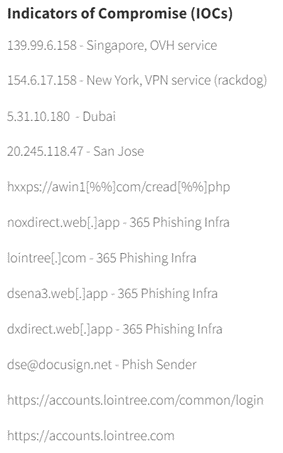
Blocking these addresses from emailing your organisation can help prevent phishing attacks sent by this threat actor from accessing you and your colleagues.
Related Links:
https://www.mitiga.io/blog/advanced-bec-scam-campaign-targeting-executives-on-o365 – Posted August 24th