
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
Ransomware attackers are once again using TeamViewer to get into the computer systems of organisations. They aim to gain initial access to endpoints and try to deploy encryptors based on the leaked LockBit ransomware builder.
TeamViewer is a legitimate tool for remote access that is commonly used in the business world because of its reputation of being easy to use and features.
However, the tool is not only appreciated by legitimate users but also by scammers and ransomware actors. They utilise TeamViewer to access remote desktops, allowing them to drop and execute malicious files without much difficulty.
A similar incident occurred back in 2016 when victims reported on various forums that their devices were breached using TeamViewer to encrypt files with the Surprise ransomware.
During that time, TeamViewer explained that the unauthorised access was due to credential stuffing. This means that the attackers didn’t exploit a new security vulnerability in the software. Instead, they used leaked credentials of users.
The software vendor clarified, “As TeamViewer is widely used, many online criminals try to log in using the data from compromised accounts. Their goal is to discover if there’s a corresponding TeamViewer account with the same credentials. If successful, they can potentially access all assigned devices to install malware or ransomware.”
TeamViewer continues to be a target for cybercriminals, as a recent report from Huntress reveals that they are still using this method to take over devices and attempt ransomware deployments.
Upon analysing log files (connections_incoming.txt), Huntress observed connections from the same source in both cases, suggesting a common attacker was involved.
In the first compromised endpoint, Huntress found multiple accesses by employees in the logs. This indicates that the software was actively used by the staff for legitimate administrative tasks.
On the other hand, the second endpoint, which has been operational since 2018, showed no activity in the logs for the past three months. This lack of recent activity suggests that it was monitored less frequently, potentially making it more appealing to attackers.
The attack on the first endpoint was successful, but fortunately, it was contained. On the second endpoint, the antivirus product successfully thwarted the attack, leading to repeated attempts to execute the payload without any success.
Although Huntress couldn’t definitively attribute these attacks to any known ransomware groups, they observed similarities with LockBit encryptors generated using a leaked LockBit Black builder.
In 2022, the ransomware builder for LockBit 3.0 was leaked, prompting the Bl00dy and Buhti gangs to promptly initiate their own campaigns using this builder.
This leaked builder enables the creation of various encryptor versions, such as an executable, a DLL, and an encrypted DLL that requires a password for proper launch.
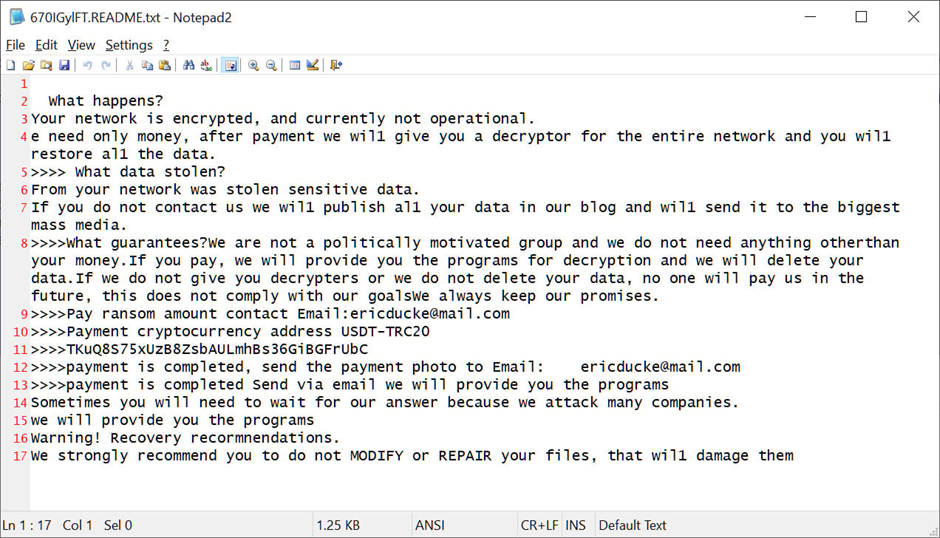
According to the Indicators of Compromise (IOCs) shared by Huntress, the attacks conducted through TeamViewer seem to involve the use of the password protected LockBit 3 DLL.
Although it remains unclear how the threat actors are currently gaining control of TeamViewer instances, the company provided the following statement regarding the attacks and securing installations:
“At TeamViewer, we prioritise the security and integrity of our platform and strongly denounce any malicious use of our software.
Our analysis indicates that many cases of unauthorised access result from a weakening of TeamViewer’s default security settings. This often involves the use of easily guessable passwords, which is only possible with an outdated version of our product. We consistently stress the importance of robust security practices, such as using complex passwords, implementing two-factor authentication, creating allow-lists, and regularly updating to the latest software versions. These measures are crucial for preventing unauthorised access.
To further assist our users in maintaining secure operations, we’ve outlined a set of best practices for secure unattended access, available at [Best practices for secure unattended access – TeamViewer Support]. We strongly urge all our users to adhere to these guidelines to bolster their security stance.”
We would advise all organisations and or individuals who use TeamViewer to update their software to the latest update immediately and when using it take extra precautions when allowing anyone onto their system and or network.
Also make sure you and your organisation are using strong passwords and Multi-Factor Authentication (MFA).
Related Links