
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
Description:
A recent rise in malware spreading through Google Ads has been noted by security researchers, with the impersonation campaigns affecting multiple software brands, such as 7-Zip, and VLC Media Player, among others.
The malware pushed by these ads is Infostealers – malware that seeks to find credentials for threat actors to use or sell online.
Threat analyst Patrick Schläpfer has researched campaigns impersonating popular free software using a method known as typosquatting, where the domain hosting the malicious files differs only slightly from the software’s name.

These sites are designed to look exactly like the site they are impersonating, even down to the malware’s name. Patrick noted that the file available for download through Audacity’s impersonator was named “audacity-win-x64.exe” to make the malware seem more realistic.
However, once downloaded, the file contained an Infostealer known as Vidar Stealer, capable of finding passwords and stealing information to bypass two-factor authentication.
Notably, the research allowed for other typosquatting domains for the same software to be found, indicating that the campaign may have numerous websites in use.
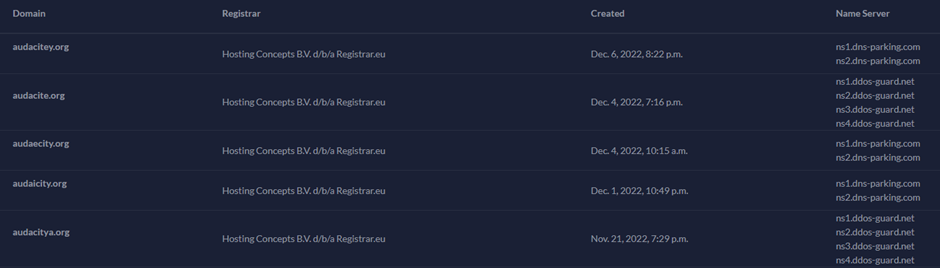
Over 92 domains have been discovered throughout the research, which Patrick notes may indicate the growing popularity of using Google Ads to spread malware.
Google has since stated that all ads which have been found to be malicious by researchers have since been removed; however, these types of campaigns are not new, and this will not be the last time threat actors use such methods.
The FBI released an alert for the misuse of search engine advertisements in December 2022 and recommends using ad-blocking extensions when performing internet searches to reduce the chances of coming into contact with malicious sites. Additionally, always check the URL of a website before downloading any files or entering any credentials to ensure that it is a legitimate site.
The FBI recommended that businesses use domain protection services to notify organisations when similar domains are registered to prevent domain spoofing and educate colleagues and customers if their business is being impersonated with spoofed domains.
Malware can pose a significant risk to individual devices, business networks, and services. Some types of malware are designed to look for other devices connected to the network of the host device to infect. This may be laptops, PCs, servers, and internet-of-things devices. An infected device brought into a work environment can pose a significant security risk and allow malicious users into your organisation’s network.
To protect your organisation against malware:
Related Links:
https://www.bleepingcomputer.com/news/security/hackers-push-malware-via-google-search-ads-for-vlc-7-zip-ccleaner/ – Published January 17th
https://techmonitor.ai/technology/cybersecurity/malware-rhadamanthys-hijacks-google-ads – Published January 16th
https://threatresearch.ext.hp.com/adverts-mimicking-popular-software-leads-to-malware/ – Published January 18th