
Important Security Alert: Issue Found in React (Common Website Technology)
A serious security fault has been discovered in a piece of software called React, which many websites and online services use behind the scenes. This…
The Trustwave Spider Labs team uncovered Tycoon Group’s Phishing-as-a-Service operation, offering advanced phishing tools via Telegram. This system is designed to sidestep Microsoft’s two-factor authentication, rapidly distribute phishing links, and dodge security measures through Cloudflare. Tycoon Group has expanded its service to include attacks on Gmail users and stealing ADFS cookies, simplifying the deployment of sophisticated phishing campaigns for individuals without technical expertise.

The Tycoon phishing system operates through a sophisticated sequence of steps starting from tricking users with deceptive links to bypassing security protocols like two-factor authentication. It uses advanced technology to disguise malicious activities and efficiently steal sensitive information. By leveraging platforms like Cloudflare, it evades detection from anti-phishing measures, making it challenging for traditional security solutions to identify and block these phishing attempts effectively.
Phishing attacks, as illustrated by the Tycoon system, involve sophisticated schemes where attackers masquerade as legitimate entities to deceive individuals into disclosing sensitive information. This process often includes sending authentic-looking messages that lead victims to counterfeit websites, bypassing security measures like two-factor authentication, to steal credentials or install malware, highlighting the evolving threat landscape and the need for enhanced cyber security vigilance.
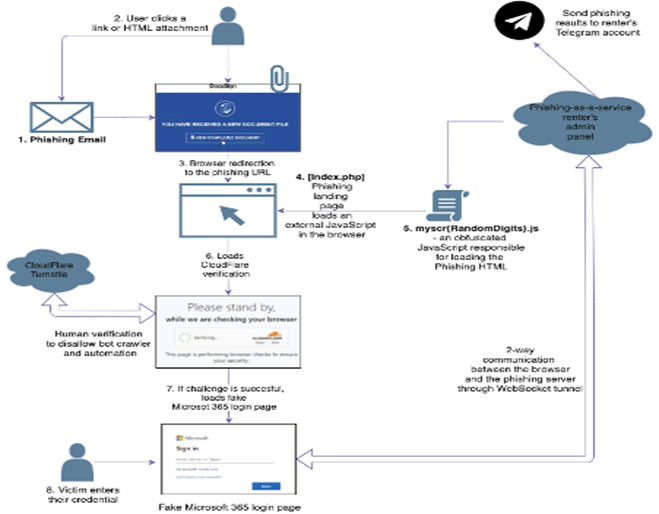
These services make launching sophisticated phishing attacks more accessible, potentially increasing the risk to Scottish businesses. Companies need to strengthen their cyber security measures, educate employees on the dangers of phishing, and stay updated on the latest security practices to mitigate these risks.
To maintain safety against systems like Tycoon, it’s crucial to stay informed about the latest cyber security practices, such as using complex, unique passwords, enabling multi-factor authentication where available, and being cautious with email links and attachments. Regularly updating software and using reputable security solutions can also help protect against phishing attacks. Vigilance and education on the latest phishing techniques are key defences in the digital age.