
We’re Hiring – Business Development & Relationship Manager
The Cyber and Fraud Centre Scotland is a non-profit organisation dedicated to promoting cybersecurity and providing comprehensive support within the business sector.
As mobile devices have become an integral, almost essential, part of our daily lives, the risk of malware infections has grown, particularly within Android devices. This guide takes you through the complex world of mobile malware, shedding light on how these infections occur, the potential consequences, and, most importantly, offering advice on protecting yourself from such threats.
While our focus is primarily on Android-based devices due to their higher susceptibility to malware, it’s essential to acknowledge that Apple’s iOS platform isn’t entirely invincible. Despite iOS’s robust security measures making it a more challenging target for cybercriminals, the possibility of compromise exists, albeit small. This guide will also discuss situations and potential vulnerabilities that might put iOS users at risk.
So, whether you’re an Android user grappling with the growing threat of malware or an iOS user navigating through a relatively secure environment, this guide provides practical advice and preventive measures to enhance your digital safety. Knowledge and awareness are the cornerstones of cyber security. We’re here to help you build that strong foundation.
While our understanding of traditional computer-based malware has grown, navigating the territory of mobile malware presents unique challenges.
Mobile malware, which operates differently than typical computer-based malware, finds its way into smartphones via less overt means. Instead of relying on phishing emails or dubious network connections, mobile malware often sneaks in through a front door: official app stores, such as Google Play and the Apple App Store.
Identifying these malicious apps can be tricky, as they often disguise themselves as legitimate apps. Everything from games, calculators, and file managers to emoji keyboards may not be as benign as they seem. The fact that these apps function as advertised initially makes it even harder to detect any hidden malicious intent.
A more disingenuous tactic observed is that certain apps may not even contain any harmful elements at the outset. This allows them to pass initial security checks and gain popularity among users. Once these apps have established a user base, the creators push updates that carry the hidden malware.
Another significant source of mobile malware comes from the practice known as ‘sideloading’ apps. Sideloading refers to installing apps from sources outside the official app stores, often from websites or third-party app stores. While sideloading can sometimes be used for legitimate purposes, it’s frequently exploited to distribute malicious apps. These unofficial sources lack the stringent security checks that official app stores provide, thereby increasing the risk of malware.

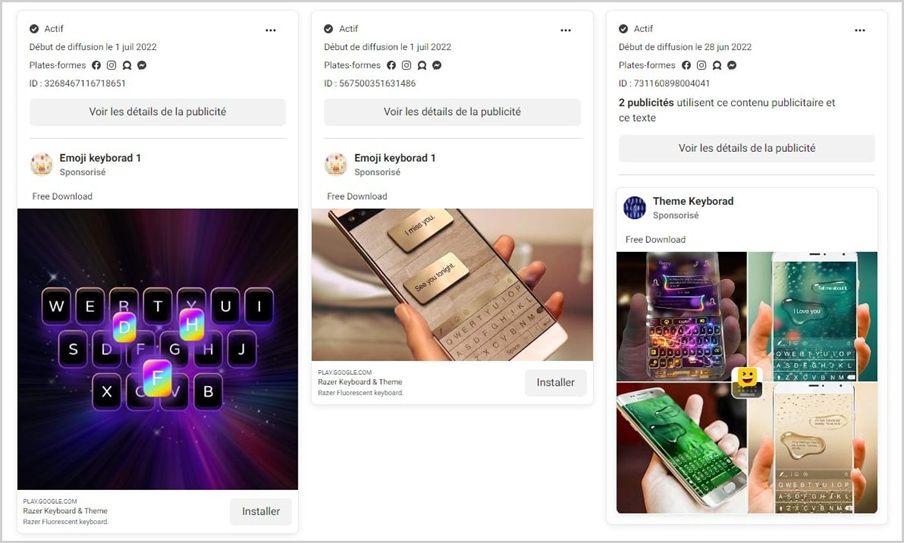
Cybercriminals also use popular social media platforms like Facebook and Instagram to promote their harmful software. With advertisements cleverly disguised to link to legitimate app stores, these covert campaigns often evade detection by the platform’s monitoring systems. As a result, unsuspecting users may unknowingly download malware-infected apps, highlighting the need for constant vigilance when interacting with app store links, even on familiar social media sites.
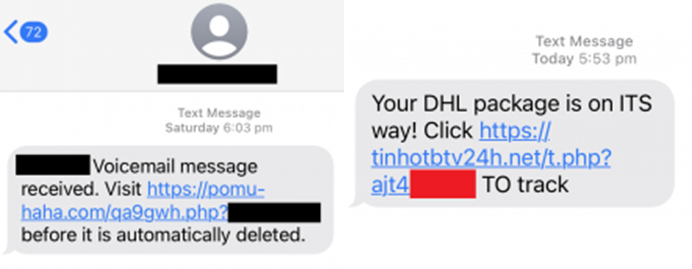
Mobile malware can infiltrate your device through seemingly innocent text messages, a common phishing technique cybercriminals employ. As highlighted by organisations like Australia’s ScamWatch, malicious campaigns often utilise persuasive text messages to distribute harmful software. Although the websites linked in these deceptive messages may vary across different campaigns, their ultimate objective remains consistent: persuading users to download an app to solve a problem outlined in the original text message. This underlines the necessity of maintaining high caution when receiving such messages and abstaining from downloading apps suggested by unfamiliar sources.
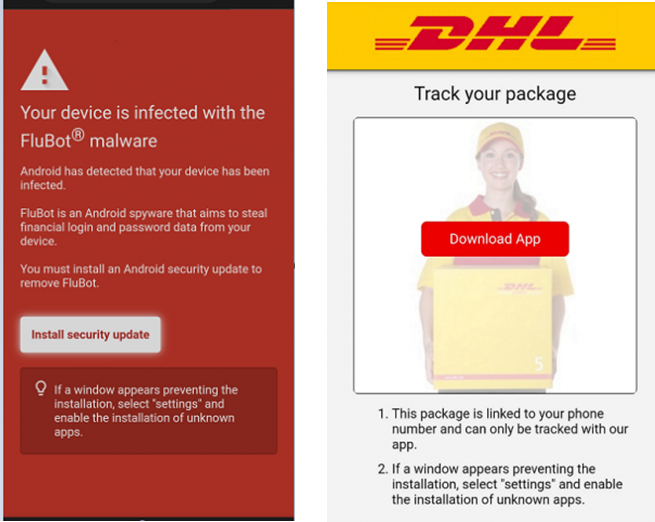
In addition to the recognised delivery mechanisms for malware, such as social media, phishing, and ‘smishing’ (SMS-based phishing), a vast landscape of unofficial Android app stores exists. These stores offer many applications for download and, unfortunately, serve as popular playgrounds for threat actors.
Within this landscape, many malware versions cleverly masquerade as premium apps ordinarily chargeable on Google’s official platform. Lured by the appeal of a freebie, users may unknowingly download these infected versions from third-party stores, mistakenly believing them to be their genuine, cost-free counterparts.
While most Android devices are designed to alert users against such risky downloads, a potential loophole exists. Users can turn off the security feature that prevents installations from unknown sources within their Android settings. While providing flexibility, this freedom also allows malicious apps to access devices.
Navigating these less-regulated app sites calls for increased caution and awareness. Understanding that free versions of typically paid apps might come with unwelcome add-ons, such as malware, is essential to securing your mobile device.
Despite a varied range of operation methods, both traditional and mobile malware share a common objective: financial gain. However, that’s where the similarities cease, and mobile malware carves out its unique path of malice.
Unlike ransomware, which tends to hold entire systems hostage in computer malware, mobile malware often adopts a subtler approach. It prefers to linger inconspicuously on the device, making minor alterations without raising the user’s suspicion. Let’s explore some of the different types of mobile malware:
Awareness of these types of mobile malware and their tactics underlines the importance of vigilance in protecting our mobile devices. As the mobile malware landscape evolves, so too must our defences.
Fortunately, the threat of mobile malware need not be a cause for alarm. With modern smartphones offering built-in protections and a measure of discretion on the user’s part, warding off these digital nuisances can be remarkably straightforward. Here are some practical steps to enhance your device’s security:
Implementing these simple yet effective measures can provide peace of mind, safeguarding your device and the personal data it holds and making your devices safer and more secure.
This guide was created in collaboration with the Cyber and Fraud Centre’s financial and banking partners.