
Data Privacy Starts With Cyber Basics
Data Privacy Day is a useful reminder that privacy and cyber security are not separate conversations. You can have the best privacy policy in the…
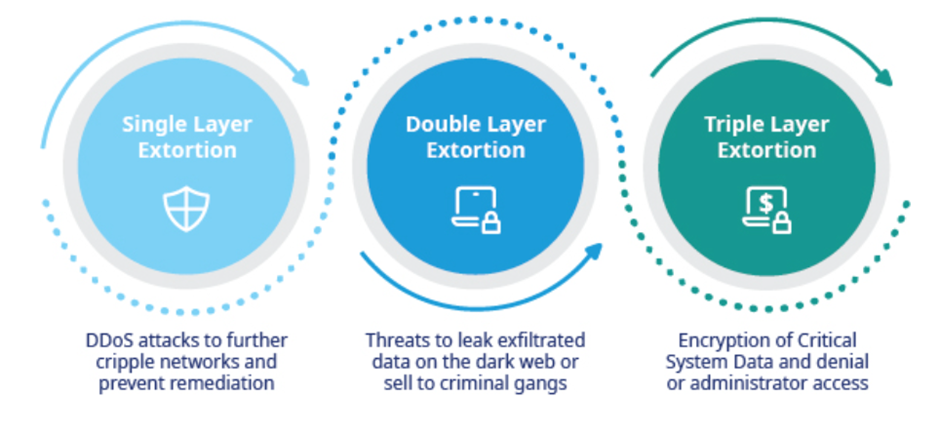
Ransomware attacks used to involve cybercriminals using encryption to lock up a company’s data, computer systems and technological infrastructure. But lately, these ransomware groups have changed their tactics. Now, they encrypt the data and exfiltrate it and threaten to leak it if ransom demands aren’t met.
This shift in strategy has proven very lucrative for ransomware groups. Companies are often willing to pay substantial sums to avoid publicly exposing their private data. This enables these groups to profit even from victims with robust backup systems that can restore encrypted data.
If a victim declines to pay, the stolen data may be auctioned off on cybercrime forums. This gives the criminals another avenue to monetise their illegal actions.
The incorporation of data extortion into ransomware groups’ playbooks coincided with a significant uptick in the number of gangs and frequency of attacks on organisations. While data exfiltration was initially added to further pressure victims alongside encryption, many groups have taken things even further with triple extortion schemes. In some cases, they encrypt and steal data, threaten employees, contact business affiliates, and overload websites with traffic (also known as Distributed Denial-of-Service or DDoS Attacks) to compel payment.
Ransomware attacks are becoming more sophisticated and frequent. Already in 2023, there have been more data extortion ransomware incidents than in all of 2022. We expect this escalating trend to continue.
To defend against these threats, organizations should implement training to spot phishing, enable multi-factor authentication, keep software updated, limit network access, maintain offline data backups, and deploy security solutions like antivirus and email filtering. With vigilance and proactive security, the impact of ransomware can be reduced.
Organisations can take proactive measures to reduce their ransomware risk:
With training, vigilance, and proactive defences, organisations can reduce their ransomware risk and build resilience against cyber threats. But no single solution is a silver bullet, requiring layered security and robust precautions.
For further insights, refer to the related article: Triple Extortion Ransomware and the Cybercrime Supply Chain